

Tim MalcomVetter
Co-Founder / CEO
Note: In true startup form, we were so busy taking calls with clients, spinning up evaluations, and shipping new features, so we are publishing this on our 13th month, not when we turned one year old. A belated happy first birthday to Wirespeed!
Wirespeed Turns 1!
One year ago we posted our Hello World announcement and published our first Press Release, setting our vision for what we had already started building: a completely automated Managed Detection & Response (MDR) platform exceeding the speed and consistency of all MDR service providers’ ability to triage cases, at a price point that slashes the legacy approaches by as much as 50%. Our messaging has refined quite a bit since then, but we’re still on target.
Let’s review how much has happened in one year!
#Our First Customer
When we made that first announcement last July, we had already signed our first design partner, a financial services mid-market company with a two decade history. They were using an unnamed top 3 MDR provider, but their CTO was friendly and allowed us to use their data to prove our MVP. I asked the CTO when their renewal for the unnamed top 3 MDR provider was due.
“October 2024,” the CTO said.
I told him, “You’ll sign with us.” The CTO wasn’t so sure.
Look, Tim, I’m happy to help you out, but you’re just getting started, and we have to lock in our decision in a month. I can’t see how you’ll do that.
In August 2024, our automated triage fired off three escalations within seconds of each other:
- Microsoft Defender complained about a user visiting a suspicious domain, but had no idea what the impact was.
- Seconds later, the victim user account logged in from New York City using a privacy VPN, instead of the company offices in Oklahoma or Kansas.
- A moment after that, a third alert, also from Microsoft Defender, indicated malware that we classify as “late stage tools” (hands on keyboard attacks).
We hadn’t even shared access to the UI yet, since we were still building it. So we immediately emailed and texted the security team. They contained the user account and isolated the affected laptop. Crisis averted. Our first breach, saved. Our first Ace of Spades.

I texted the CTO: “Tell us when [Top 3 MDR Provider] tells you about this.” We were sure their provider would see it. We just wanted to know how much faster we were. Would we beat them by minutes? Hours? How long? We waited and expected to hear back at any time.
The next day, I texted again: “Did you hear back from [Top 3 MDR Provider] yet?”
No, they still haven’t sent us anything about this breach. We are definitely signing with you!
Just like that, we closed our first customer. September 2024, barely one month out of stealth. We also cut their MDR bill in half, which was very much appreciated given the state of the economy!
In the last year, we have tracked several confirmed breach saves, each getting their own Ace of Spades in our Wirespeed historical journal.
#Our First ChatOps Win
One of the pain points we set out to solve is universal among MDR providers:
It feels like we pay you to investigate alerts, only for you to send them over the wall to our team to investigate.
This was a pain point that we lived, previously, and confirmed from a number of security teams who used a variety of third party managed SOC solutions. We also confirmed it was a pain point for MDR providers themselves. Then we thought about what some of the world’s biggest and best SOC teams do, like what I experienced red teaming the world’s largest company: the SOC teams chase down the impacted users (victims) and get the missing context to turn a murky detection into an objectively clear-cut case. So we built an automated version of that, using Slack, Teams, Email and SMS, calling it ChatOps.

In November 2024, our thesis that victim users often know best about detections proved out and we contained a BEC account takeover in 214 seconds. We were ecstatic! Another Ace of Spades and proof that this approach not only works, but drastically cuts down MTTR (Mean Time to Respond), which greatly reduces the likelihood of material impact coming out of a scenario like an MFA credential phish account takeover (ATO) incident.
To add even more color to this story, the victim in this case is an accountant at that same first customer. About a year prior, under the monitoring of the unnamed Top 3 MDR provider, this same exact thing happened: an MFA phish, ATO, followed by BEC (Business Email Compromise).
In the earlier event, the attacker found invoices recently sent from the accountant to clients, edited those PDFs with the attacker’s bank account and routing numbers, and then resent them to the clients saying she made a mistake “please use the updated version instead.” Naturally, the attacker added mailbox rules to mark the emails as read and hide them in the RSS feeds folder in Outlook, where no one has looked since 2010. A couple months later, when tracking down why the clients were late on payment, the client and accountant swapped notes and realized the money was long gone. In total, more than $1M in wire fraud was claimed on their cyber insurance policy.
But this time, we contained the bad guy in 3 minutes.
We have had many more Ace of Spades moments coming from automated triage, ChatOps, and automated containment, some of which are listed in our published Success Stories.
ChatOps works! So much so, we observed an AI SecOps vendor attempting to copy this feature into their platform this past quarter.
#The AI Gold Rush
When we set out to build Wirespeed, we had a specific vision in mind to map all possible security alerts to our own taxonomy and have that drive a series of investigation steps and decisions that would be made in conditional logic (i.e. if [x] else if [y] logic trees).
Then came the AI gold rush.
Security decisions must be predictable, which is why we chose deterministic, conditional Logic over AI. Refining our position, we added some AI-enabled features, but only for Type 2 Decisions (security decisions are “Type 1”). A year ago, we started noticing very technically astute buyers coming to us because they agreed with our position, but didn’t want to publicly acknowledge it. Now, one year later, we frequently hear: “AI is an amazing technology, but not for everything.”
We have more than hammers in our toolbox. Not every SecOps problem is a nail.
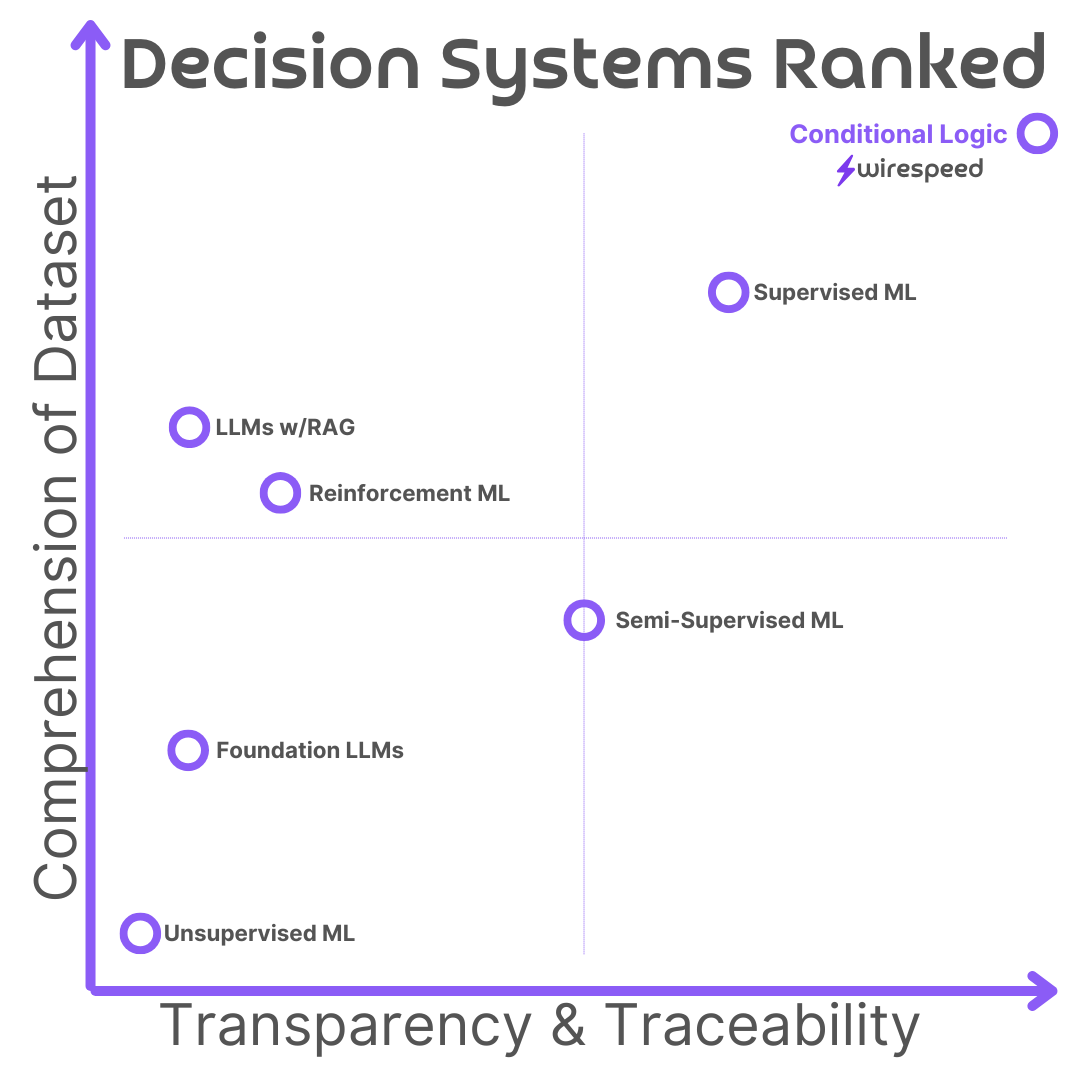
At its core, Wirespeed is managed process. That’s why we cite Bruce Schneier as one of our influences, because of his famous saying:
Security is a process, not a product.
Wirespeed is both a process and a product.
#Acceptable Quality Limits (AQL)
This first year has proven that AQL (Acceptable Quality Limits) is the perfect complement to Wirespeed, ensuring the quality of our ingestion and verdicts stays high. Because our system uses deterministic logic, finding a defect means we can also find its root cause, unlike non-deterministic systems based on LLMs, where troubleshooting is a coin-flip to see if you can actually fix the problem:
- Maybe it’s the prompt
- Maybe it’s the model
- Maybe you fix it today
- Maybe the AI platform you depend upon changes tomorrow and everything breaks
We built AQL directly into our platform. It’s not an afterthought. It’s not a jupyter notebook or a spreadsheet. It’s how we work. It’s how we keep the human expertise engaged, at scale. It’s why the quality of our cases and verdicts is something we are so proud of.
#Our “Wirespeed-fast” Data Lake
When we started out, our goal was to do the “R” part of “MDR” the best: Response. We wanted to automatically triage and contain threats as quickly as we could. We built that first. We saw success and stopped bad guys with it.
From there, the market told us very clearly that customers want a place to keep their logs for compliance reasons. We also needed additional telemetry from our customers environments so we could make better decisions to reduce the noise and false positives.
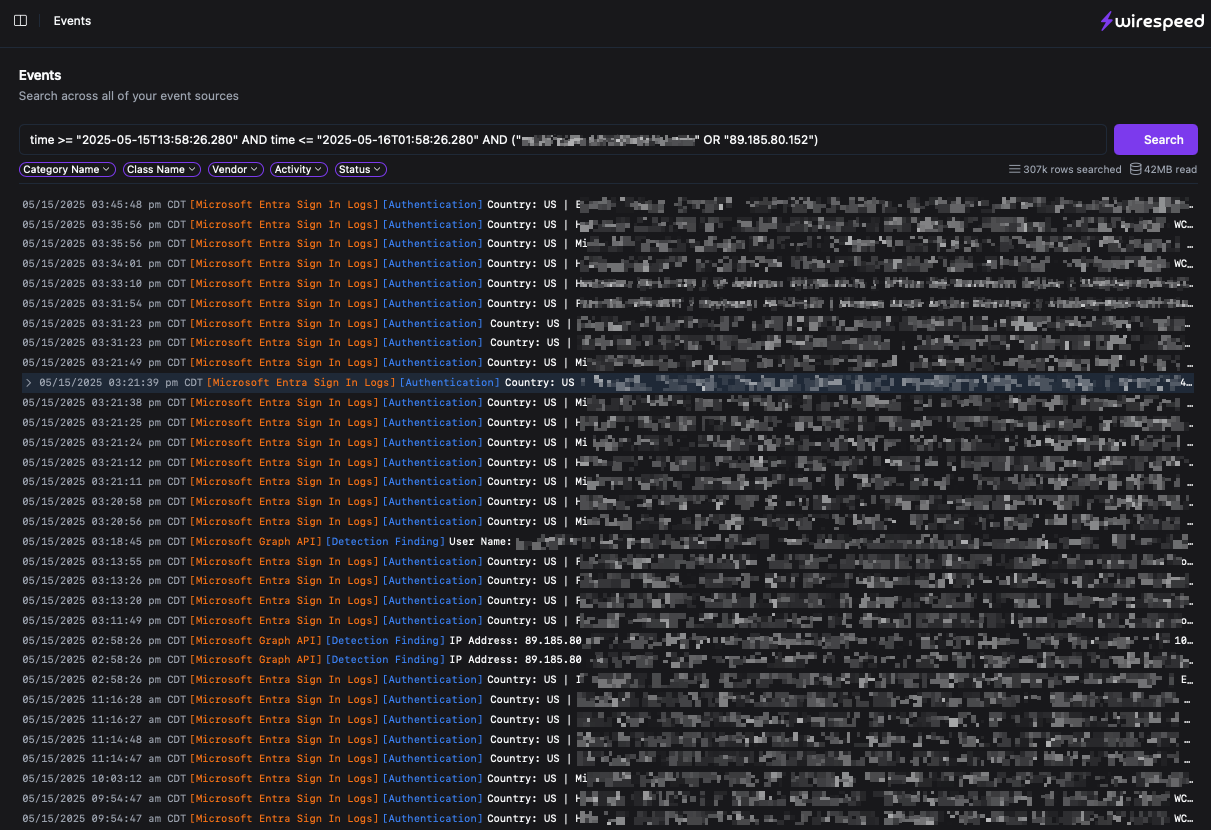
So we shipped our own Data Lake (shown above), built on the amazing Clickhouse data warehouse, with all data stored in OCSF (Open Cyber Security Framework) format, directly aligned with our intent to support best-of-breed solutions in the most open model possible, not vendor locked-in like many of the really big players. This reverberated with our desire to be the “anti-vendor vendor” as we often tell our customers:
We wouldn’t buy from a locked-in vendor using closed models with non-transparent process or results, so we won’t build it that way.
#Price Complexity
We hate price complexity. We scoff at many of the big name competition, who create invoices with one SKU for the MDR/SOC services, a second SKU for storing your data, and a third SKU for you to be able to actually see your data! (Yes, some vendors really do this!) So, we offered up 90 days’ log retention for free with the ability to retain as long as you need, per log source, for a super nominal, industry-leading price.
#Our New Take on Detections
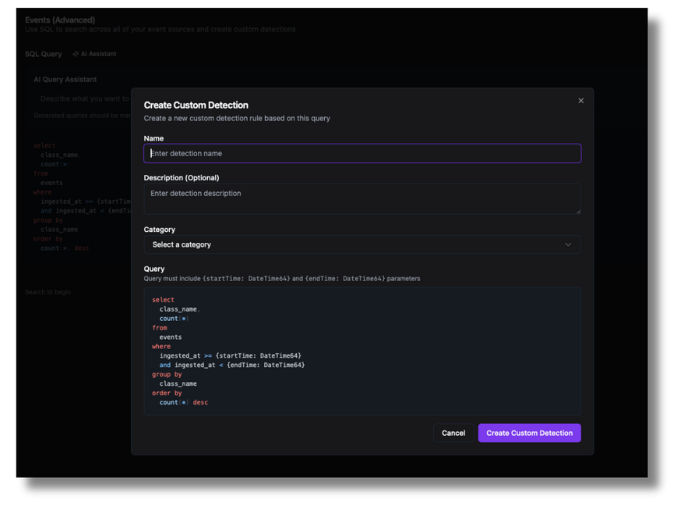
We recently shipped our own AI-enabled Detection Engine, giving you full access to all of your security data in Clickhouse with a natural language interface prompt on top to help you built complex queries you can put into production as custom detection rules. As an industry first, Wirespeed will automatically triage alerts when your custom detections fire, knocking down any noise from rules that are too loose, removing one of the biggest pain points in detection engineering. Where else can you triage detections faster than you can build the detections themselves?!?!
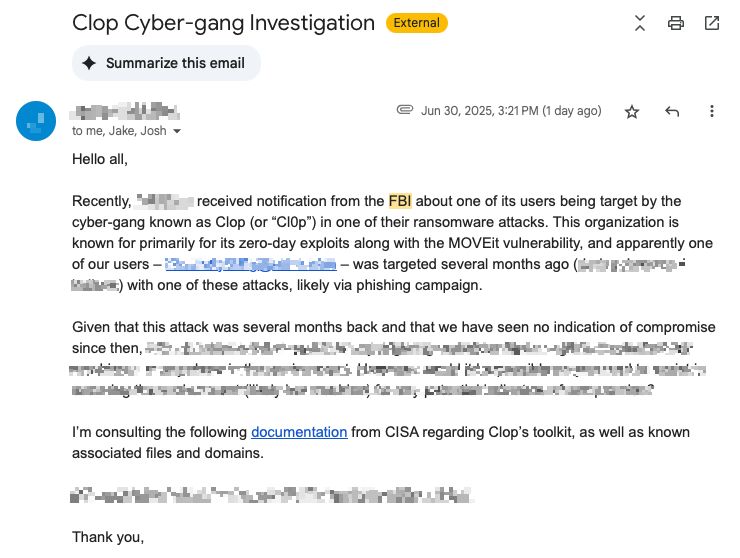
#That time we stopped Ransomware in 8 Minutes & the FBI visited!
In March 2025, we thwarted the infamous Cl0p ransomware group in 8 minutes, completely automated, another Ace of Spades and confirmation that our approach is winning! Then 3 months later in June, the FBI sent a special agent to visit this customer’s headquarters to let them know about a ransomware attack targeting them. It certainly gave our customer pause, but then a bunch of relief when they realized it was the threat we already contained.
#Raising the Seed Round
Many may not realize, but Jake and I bootstrapped Wirespeed to revenue, acquiring several customers before closing our “over-subscribed” investment seed round. For us, raising the seed round was more about the validation and power of our network. The capital came second as we had plotted a path to grow more slowly without it. In our seed round, we have combined many talented serial entrepreneurs both in and out of cybersecurity in an overwhelming statement of validation of our approach and our roadmap. We’re overwhelmingly grateful and energized everyday to have this team of investors behind us, which enabled us to pull forward key hires and grow the team.
#Marketing & Brand
This past year, we published over 50 blogs and many more social posts, podcast appearances, and in-person events, talks, and appearances, as we hone-in exactly what the Wirespeed brand is. We know one thing for certain: it’s our brand. We’ve seen too much “me too,” empty, buzzwordy, pushy, “what does it really even do?” marketing over our careers, and Wirespeed is not that. We’re grateful to have your eyes, ears, and attention, especially that you’ve read this far! Thank you!
#SEMPRE AVANTI
Always Onward.
Wirespeed has been doing 24-7 security monitoring since 7-24 (July 2024), but we’re just getting started. Keep watching to see where we go next!
