

Tim MalcomVetter
Co-Founder / CEO
Cybersecurity is too full of failure stories, here’s a real-life success story from March 2025 instead!
[EDIT July 2025: Be sure to read down to the bottom for an update to this story involving the FBI!]
Ransomware Thwarted in 8 Minutes
#The coordinated setup …
The day before a group of threat actors clearly bent on locking our client out of all of their systems so they can ransom them back, the threat actors very quickly and systematically registered the email addresses of our client’s employees in dozens of noisy email marketing lists. The result is a sudden flood of spam email from dozens of sources—too many to find a single chokepoint to block.
Employees struggle to find legitimate email in their inboxes, deleting hundreds of unwanted emails while Outlook constantly pings them with announcements of many more. The threat actors very much intend for this influx to be chaotic and disruptive, so they can use this as a reason to make contact as the “IT Help Desk” to save the day, tricking victims into installing malware that would grant them access and the time to explore the environment, escalate permissions, and deploy ransomware everywhere.
#This was the SECOND TIME our client experienced this.
The first time was in October 2024.
That time, when the spam influx happened, our client reached out to us for advice. We immediately recognized the parallels with this report on the Black Basta ransomware group who used this unique tactic. So we urgently advised our customer to take the following countermeasures:
- Block third party connections to Microsoft Teams, allowing only specific business partners’ domains.
- Notify all of the users to NOT respond to inbound Microsoft Teams connections that say they’re part of the company IT Help Desk.
Our client followed the directions exactly.

Then all they could do is sit, purge more spam emails as they continuously streamed in, and wait. We waited for hours. We knew they were coming. All computer systems are constantly targeted the second you plug them into the internet, but this was different: how many other situations in cybersecurity can you know your adversary is coming? It’s an eery feeling.
It immediately reminded us of that scene in Lord of the Rings where the hordes of orcs approached the castle walls. You can hear them. You know they’re there. It’s just a matter of time before they push the ladders up against the walls. And your job is to kick the ladders down, run to the other end of the wall, kick more ladders down, run back, and repeat until they give up.
So we kept waiting for hours.
Then it happened, just before the end of the workday. Many employees started getting inbound Microsoft Teams requests that appeared to be the IT Help Desk, only this company’s help desk doesn’t do that and everyone was forewarned this would likely start today.
Fortunately, on that day, NO ONE fell for the ruse. Everyone did their part and kicked the proverbial ladders off the castle wall until Black Basta gave up and moved on.
#Fast forward 4+ months…
We got another inbound request for help. The massive influx of spam was back! That sinking feeling returned to the pits of our stomachs, for both us and our client.
Just like last time, we waited.
Also just like last time, at the end of the workday, Microsoft Teams calls launched, masquerading as the IT Helpdesk. This time, they got a victim to take the bait.
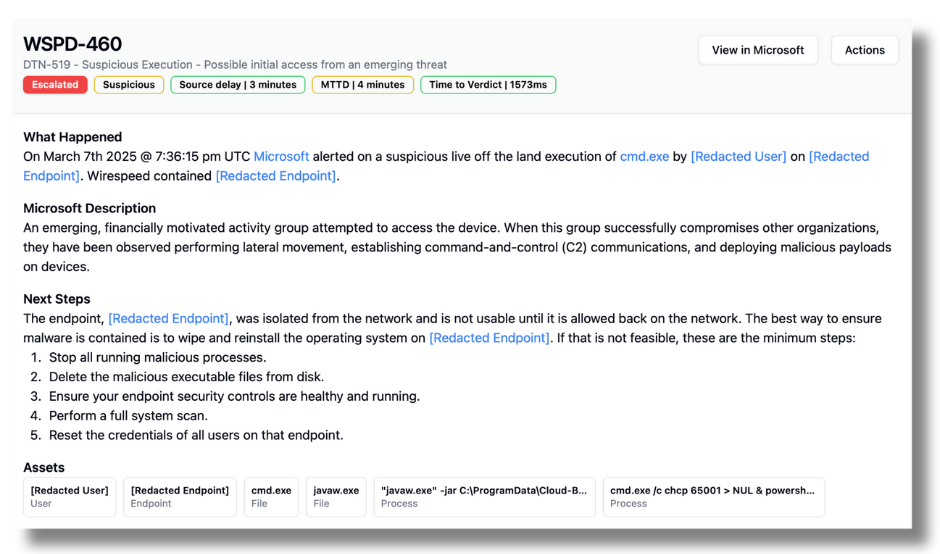
The threat actor convinced the victim to run a software tool that they claimed would fix the spam problem. That “tool” dropped the legitimate javaw.exe binary (sha256: ed20288d2cad9a5f9a9577be2398102717724abba009b6e12842219ac07d13fc) along side a malicious .jar file (java archive with a java executable in it):
"javaw.exe" -jar C:\ProgramData\Cloud-Based-Mail\Cloud-Based-Mail.jar
We’ve seen other ransomware reports that show similar file names relating to fixing email, new name iterations to avoid detections.
The Java .jar file then ran a command that set the console to use UTF-8 international charsets. This may be an indicator of a third party from a non-English location or possibly just using UTF-8 as a trick to avoid prior detection logic. That same one-liner also began a powershell session:
cmd.exe /c chcp 65001 > NUL & powershell.exe -ExecutionPolicy Bypass -NoExit -NoProfile -Command -
We ingested the detection from Microsoft Defender, enriched it with some third party sources, and processed it, coming to our verdict conclusion in 1.5 seconds (1573 milliseconds to be precise). [NOTE: that is actually a slow one for us, as we’re typically about half that speed. The queues must have been a little busy at that instant.]
In that 1.5s, we enriched the files to confirm the javaw.exe version was safe and benign, and confirmed the use of cmd.exe and powershell.exe as the authentic Microsoft binaries, making this a “live off the land” execution. Since we didn’t have the hash for the .jar file (and it may not have proven useful at the rate they’re making subtle changes to it), we couldn’t confirm true malice, just yet.
In cases like these, if know the user is a technical user, we will actually ask them over Slack, Teams, or Email if they were aware and intentionally executing this. One of the things that makes Wirespeed special is that we sync directories and perform persona matching to locate technical users, admins, VIPs like your C-Suite, and Financial users who have access to systems that send and receive money. But in this case, as you can see from the timeline below, we knew this wasn’t someone to ask about this and we didn’t have the time, so we escalated the case.
This is the actual timeline from the case:
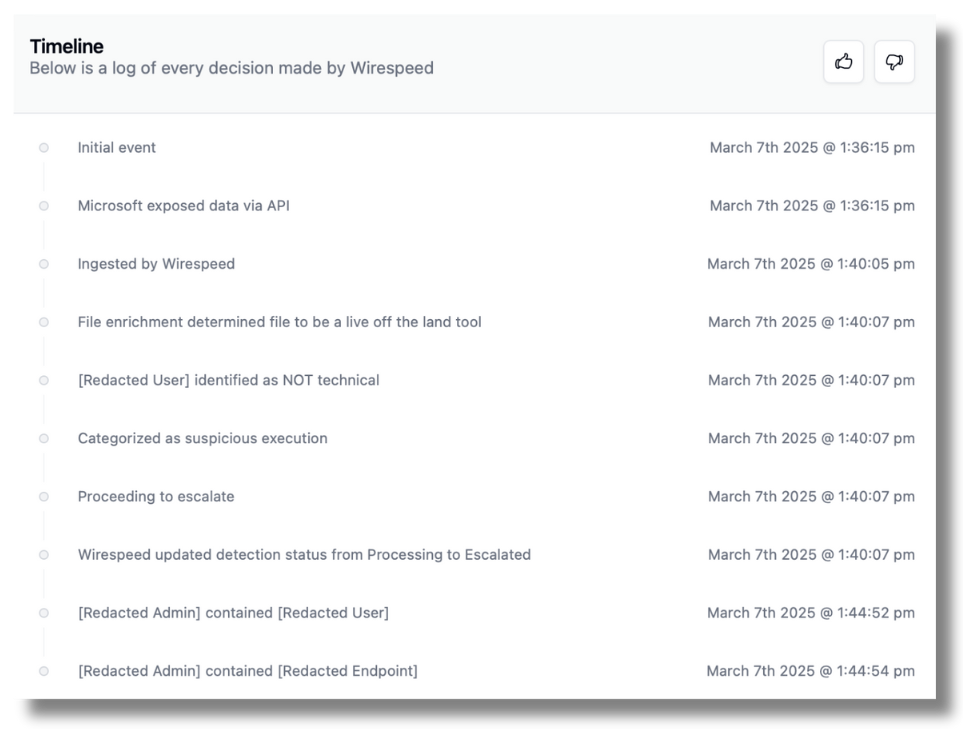
Within minutes, the endpoint and the user were both contained and the situation was over. Black Basta (or the copycat) moved on.
Again, this was a slower case for us than our average with its 8.5 minute cradle-to-grave time span, yet we’re happy to talk about it because: A) we’re still way faster than other MDR solutions, and B) the primary reason—our customer didn’t have ransomware, didn’t invoke third party incident response, and didn’t call their cyberinsurance provider for a claim. They didn’t even have to work late.
We took care of it!
#UPDATE: FBI Visit
More than 3 months later, the FBI came to visit our client, informing them they “were a target of a ransomware operation.” This, of course, came as a shock to our client, and made them concerned thinking this was an imminent threat. After swapping notes, we came to realize the FBI were referring to this story, in which Wirespeed contained the ransomware actor in 8 minutes!
Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.