

Tim MalcomVetter
Co-Founder / CEO
214 Seconds in November
Cybersecurity is too full of failure stories. Here’s a feel good win instead: we hope the criminal who stole our customer’s credentials enjoyed the 214 seconds of access they got with them!
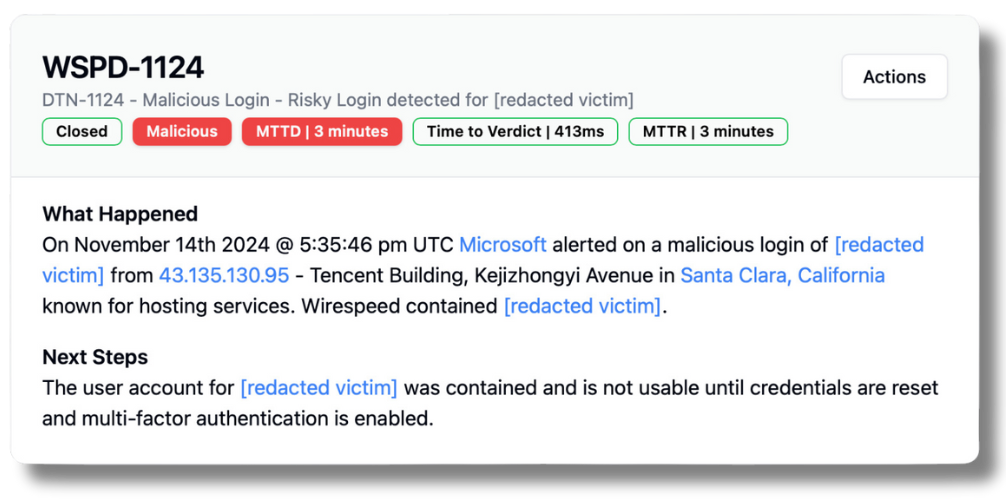
We don’t (and often can’t) know exactly how a victim’s credentials were stolen, but we can definitely see the suspicious logins. We suspect this one was likely adversary-in-the-middle real-time phishing for MFA credentials.
There was a 160 second delay from the time the suspicious logon event happened (this is “boom”) and the time Microsoft made a detection available for consumption via their API. That’s the bulk of the duration of the attacker’s 214 seconds—waiting on Microsoft!
This is the actual (redacted) timeline from the case:
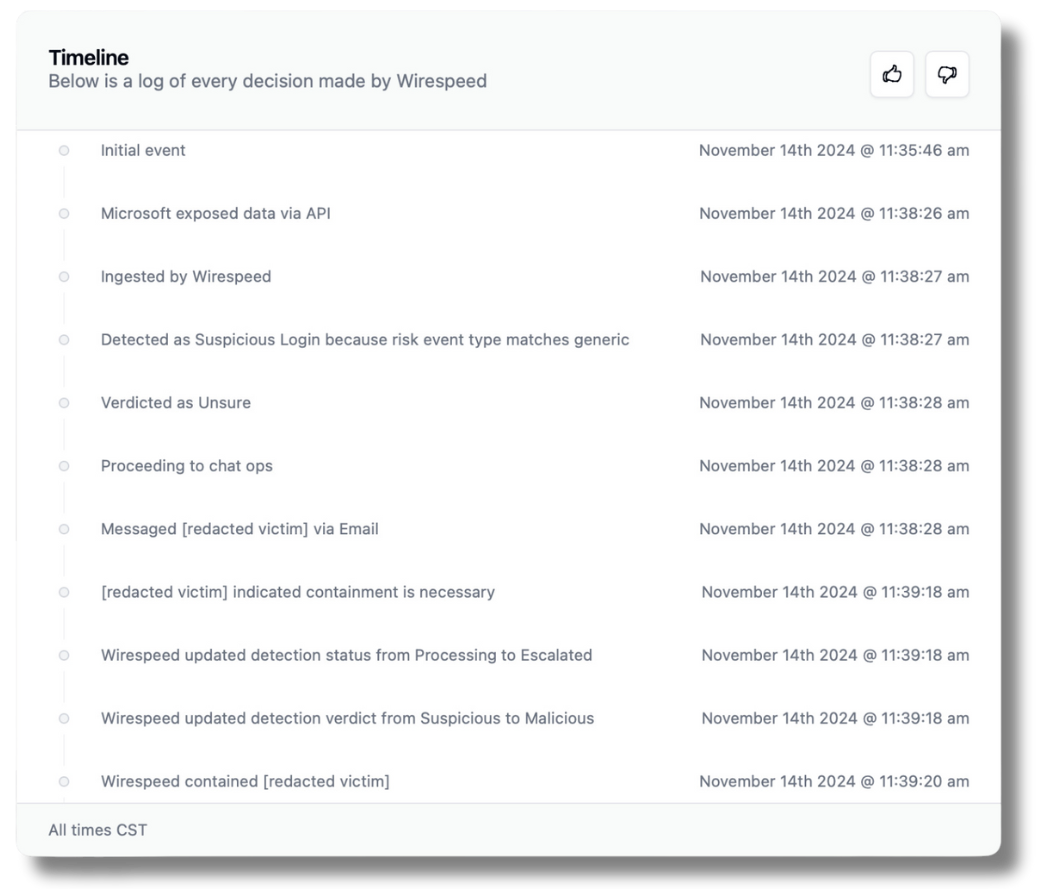
Within ~1 second, we had assigned a verdict of Suspicious (unsure) and messaged the victim user directly if they logged in from an IP address belonging to Chinese tech company, Tencent, in a data center they operate in California, with an abuse contact in Singapore (all the components necessary to be a quasi-bulletproof host for criminals).
The victim immediately responded that the login wasn’t her, so we thanked her, rotated her credentials, and killed her sessions, ruining the illicit access the criminal gained.
Technically, an attacker can establish additional means of persistent access in seconds, but that requires the attacker to be disciplined, organized, and automated, which fortunately most aren’t (because they don’t experience fast enough friction). Most likely, this particular criminal wasn’t closely watching the adversary-in-the-middle phishes, the suspicious login was generated as the victim was tricked into logging into a fake login form, and the criminal never even had interactive access with the stolen credentials.
But that same attacker likely had success for their BEC or Ransomware goals using these same tricks and infrastructure … against some other victim who wasn’t using Wirespeed MDR.

Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.