
Tim MalcomVetter
Co-Founder / CEO
The Detection Iceberg
Poll 100 cybersecurity professionals responsible for monitoring their environments’ security, and I’d wager that 90 wish they had better visibility, 5 aren’t sure (and are afraid to comment because they’ll think the lack of visibility is their fault), 3 are brand new and haven’t formed an opinion, and the last 2 are arrogant — and very likely to be reset by a future breach.
So the question is: what should be done about the lack of visibility?
First and always: we must recommend better detection telemetry, of course. Wirespeed MDR was intentionally designed to be leaner and massively less expensive than other MDRs, for the purpose of resetting our clients’ spend towards better detection products to increase their visibility. This is why we wrote Where do Detections Come From? and discussed right sizing the spend to be closer to $0 in the DIY and Service Provider buckets, and nearly 100% of the Detection budget spent on purpose-built detection products.
Second, and why we wrote Life of a SOC Analyst, is that Security Operations deals with reality, the current state of things now, not in some hypothetical situation. There’s something refreshing and invigorating about that which draws me in more than any other aspect of security. It’s real. It’s happening now. So we must have an answer for what to do when visibility is poor.
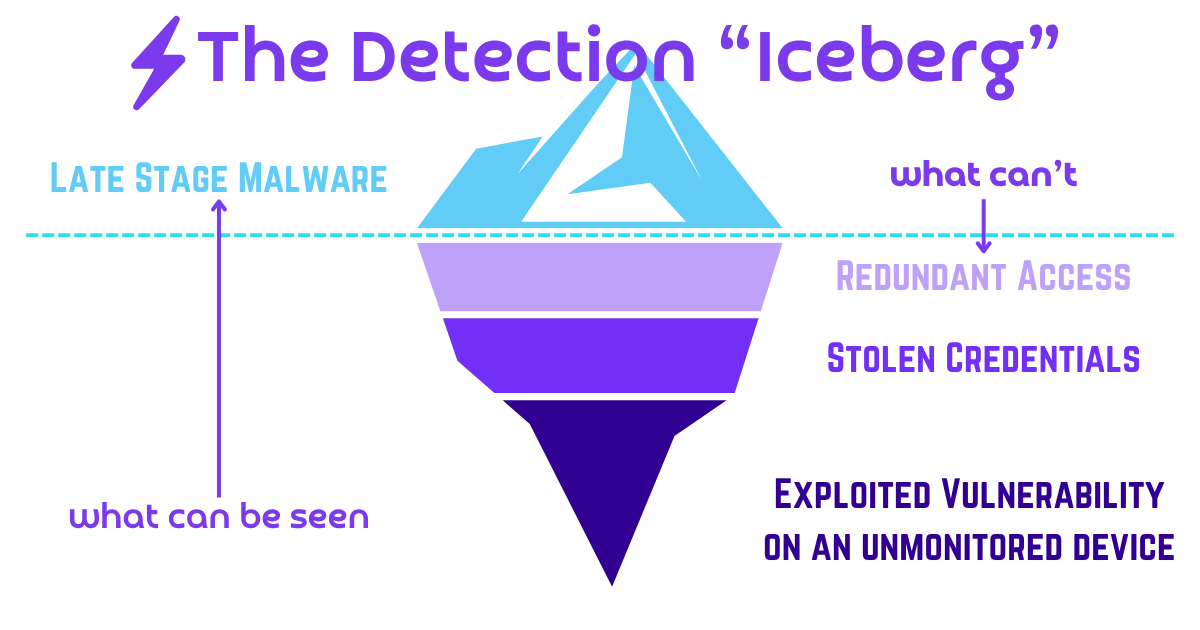
That answer is to understand the Detection Iceberg.
#Above the Water Line
As the analogy goes, there’s more iceberg under the water than above the water. Above the water, the telemetry or signal that something bad has occurred might be minimal, sometimes as little as a single alert that someone or some product might classify as “low” or “informational.” This is part of the reason that we, at Wirespeed, are not super keen on the use of severities (more on that topic another day), but cybersecurity has depended on severities for decades now as a means of doing poor triage: only look at the Critical and High alerts, everything else is designed to be ignored, or else alert fatigue sets in.
At Wirespeed, we want to address this vast quantity of signals, including the “lower severity” alerts. We want to address and triage all alerts to a complete verdict.
But in order to do that, it’s necessary to understand what the alert signal may not be telling you. We put our critical, skeptical hats on and assume that attackers may be able to bypass various levels of detection controls, and if so, when we get a hit, we want to respond properly and succinctly.
#Below the Water Line
When we receive an alert, we assume there was activity that was not instrumented, hence no telemetry or detections for the related behavior leading up to that alert. A common example with ransomware actors recently has been to compromise an edge device, such as a VPN/Firewall with a missing exploitable patch. It’s often very difficult to know when those devices are exploited and compromised, because network traffic to them is usually encrypted, therefore invisible to IDS/IPS/NGFW network monitoring without complex work with certificates and real-time decryption, and also because the underlying Operating System (typically linux) is considered off-limits to end-customers who are buying it as a “product” so it’s very unlikely that EDR (endpoint detection & response) will be deployed there to watch for suspicious activity.
So, when we see an alert indicating an attacker is in the later stages of an attack — without corresponding activity leading up to it — the smartest assumption a defender can make is that it’s only the tip of the iceberg, and that there is much more going on under the water.
#Bringing the Adversarial Mindset
What makes Wirespeed unique is that we bring both an offensive and defensive mindset to our Automated MDR. In my red team days, if we didn’t experience “defensive friction” (as we used to call it) within the first few hours of gaining unauthorized access into our target organization, we generally would feel relaxed and knew we could take as long as we needed to reach our goals.
Sometimes, we would experience incomplete “friction” — a defender would see a signal of something bad going on, but they would make a rushed containment decision that was incomplete. When we experienced that, we definitely got a positive rush of both adrenaline and dopamine, because we knew we were ahead of the defender with a massive advantage.
Don’t be those either of those defenders — the ones who have no signals at all, no response to the signals, or the ones who only respond to the tip of the iceberg, not stopping to ask about what’s under the water. As pretend bad guys, we always ended up beating them and reaching our objective.
Stay tuned for future posts and more examples of how Wirespeed approaches the Detection Iceberg.

Want to know more about Wirespeed? Follow us on LinkedIn / X or start a FREE TRIAL today.