

Josh Moore
Founding Security Engineer
3 Case Monte!
A story of truly democratized security v.s. a coordinated attack
#Prelude
Last week we shared how a prospect spun up a Wirespeed free trial and shortly after experienced a breach—an account takeover with an immediate attempt to spread laterally by phishing other internal victims—that we shut down in just 14 minutes. That’s pretty fast value and an awesome story, but we can do better. In fact, we just did.
On that note: When was the last time your MDR said, “we can do better”? If they aren’t pushing the industry forward with innovation and choose to ignore problems long observed in the space, they’re likely just hitching their wagon to whatever the latest hype is hoping it keeps you around…
Now without further ado…
#3 Case Monte
TL;DR at the end!
#Case 1 - First signal
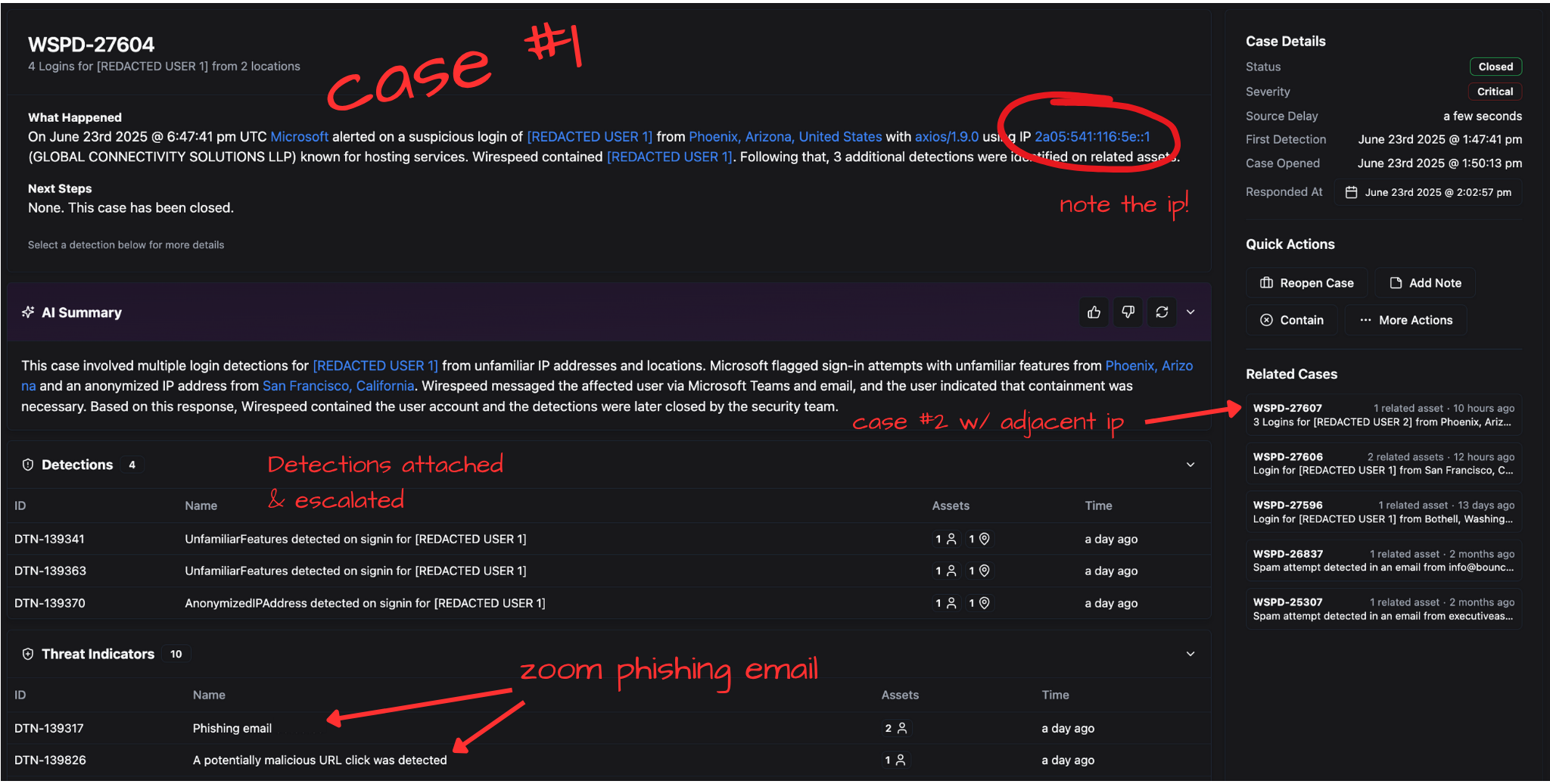
I won’t rehash every detail in the image, but here we’ve got a tale as old as time. Numerous detections from Microsoft painting a picture of an account compromise. Note the IP address – we’ll come back to that. We can see the malicious email observed that got this party started. If we double click that, we can see a little more detail in the detection’s event log:
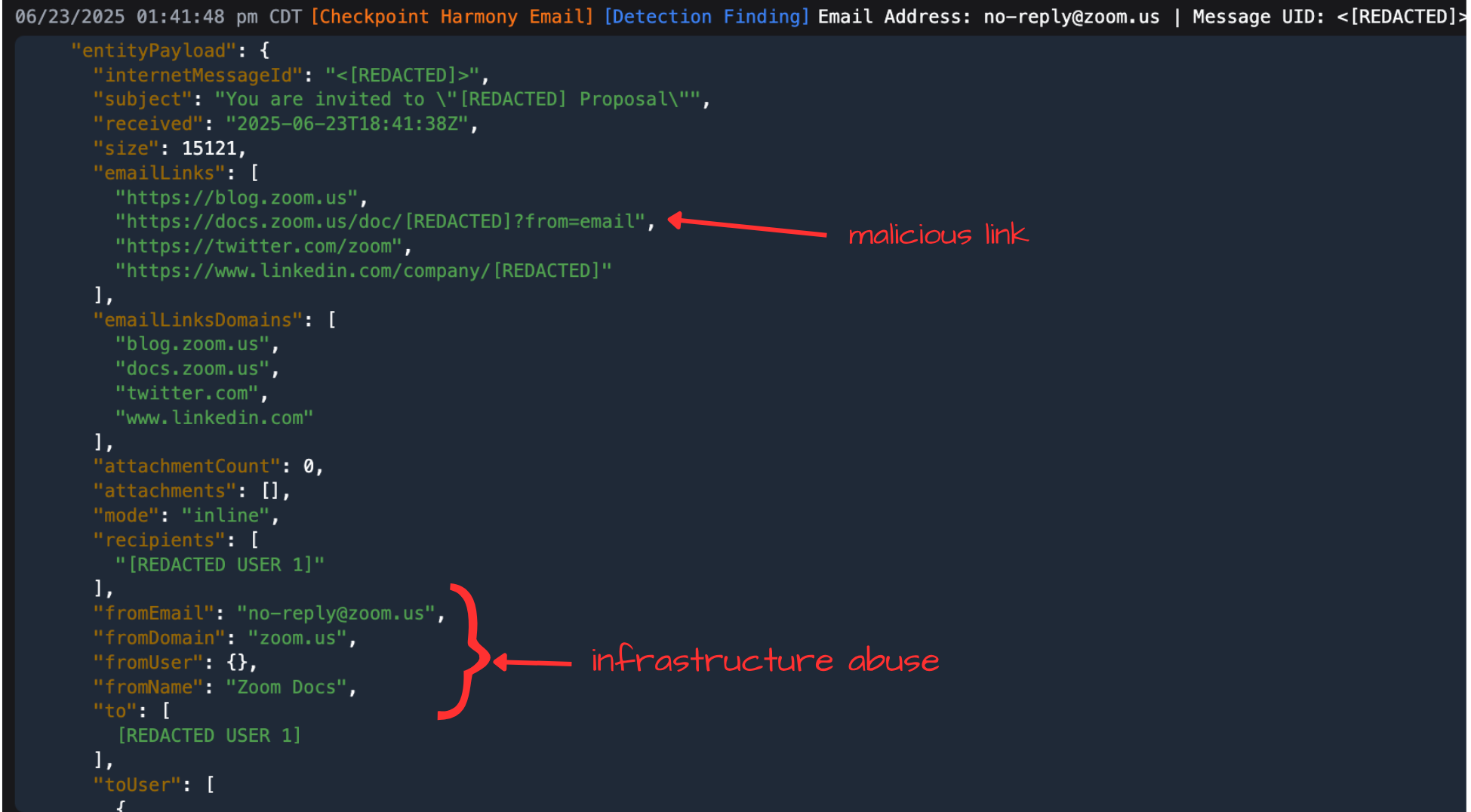
Huh, interesting – Zoom Docs from no-reply@zoom.us. This feels a lot like infrastructure abuse we’ve seen before. Threat actors often use document hosting services (especially enterprise ones they gain access to via accounts of their previous BEC victims!) to disguise malicious links as legitimate ones to important files.
While the technique isn’t exactly novel, it does seem like abuse of Zoom Infrastructure specifically is recently “trending”.
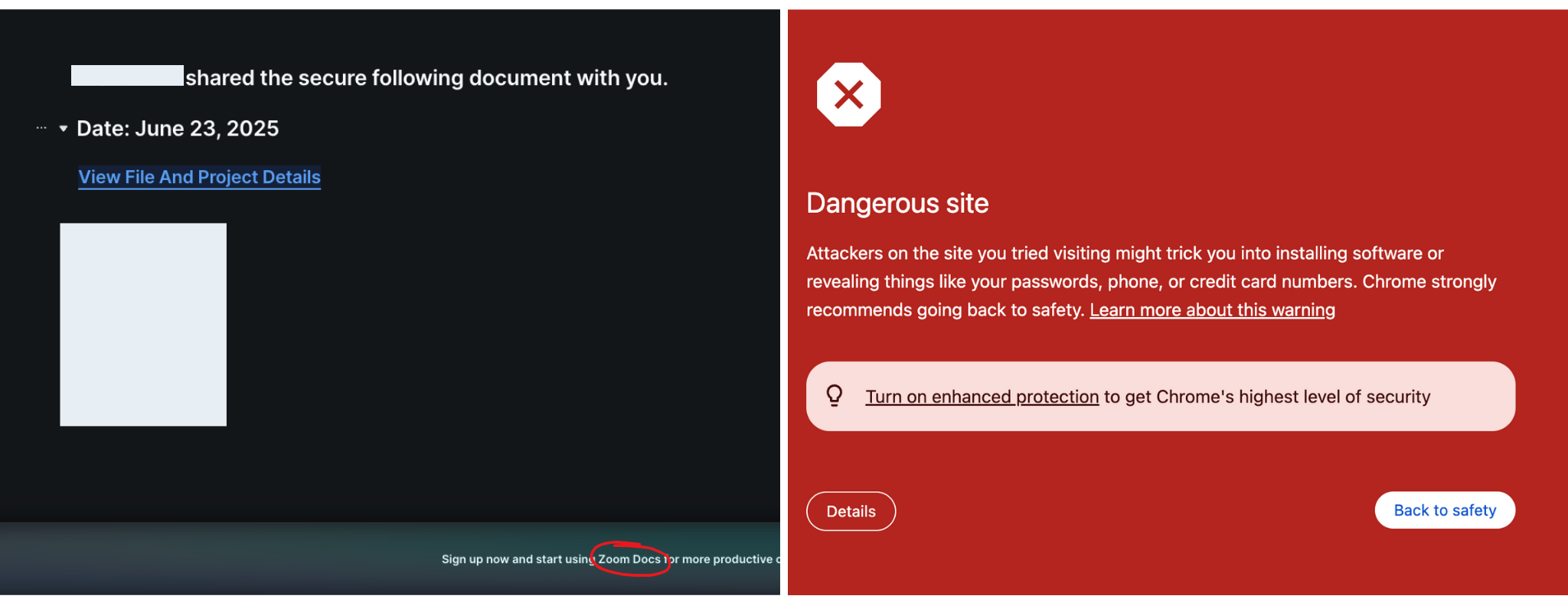
Only a couple of clicks, and the victim is redirected to an attacker in the middle (AiTM) proxy that’ll steal their credentials and session tokens.
Unfortunately, this one resulted in access to [Redacted-User-1]'s account, but before you give a point to the bad guys, fortunately, [Redacted-Organization-1] uses Wirespeed – the MDR that can triage and respond in seconds.
Here’s how we handled this one:
#Our Response
Quick aside: If you’ll notice, this case was closed by a user from [Redacted Service Provider]. While this is an important detail to the rest of the story, we want to stop and say that we LOVE working with Service Providers. If you’re from one and are interested in learning about how you could use Wirespeed for your clients, let us know!
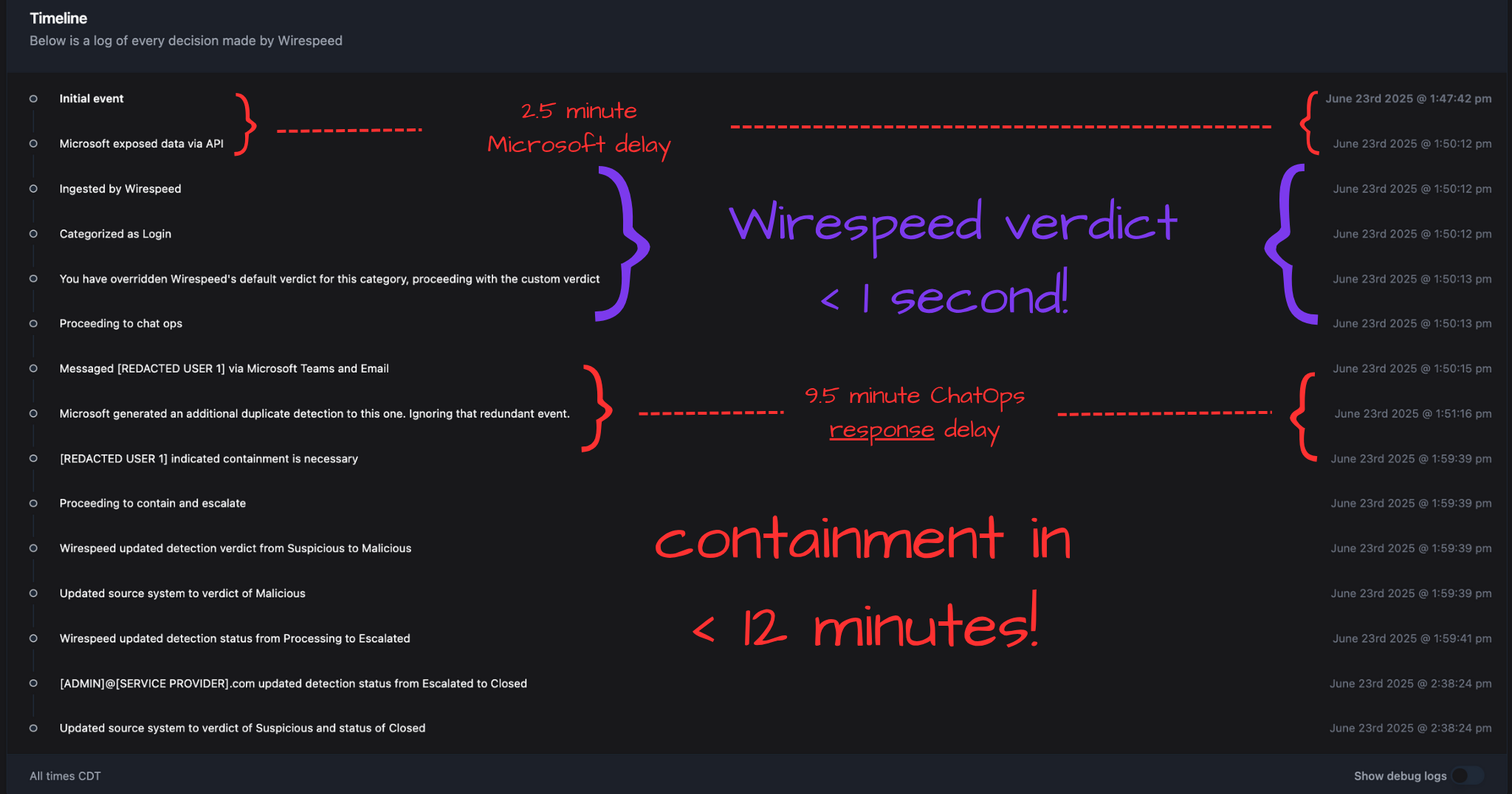
What do we see? Well at a high level, the threat actor (TA) gained access to the account @ 1:47:42 pm and was promptly given the boot only a 11 minutes and 57 seconds(!!!) later @ 1:59:39 pm—and that included pinging the victim user over Microsoft Teams and Email and waiting for them to confirm the login wasn’t one they expected.
Notable timeline details:
- The longest delay was waiting on the end-user to indicate containment was needed - ~9.5 minutes (Note: this customer was configured to contain the account after a 15 minute timeout.)
- The second longest delay was waiting for Microsoft to surface the alert!- ~2.5 minutes
- Time it took us to decide there’s not enough context and to use ChatOps - <1 second
- Luckily [Redacted-Organization-1] enabled our automated-containment feature so…
- The delay to initiate containment - <1 second
Why does this matter?
While this response speed is exceptional compared to a traditional MDR or Managed SOC, it’s our standard at Wirespeed. While we could toot our own horn about our fast response time in this example, we’re really talking about this case today because it sets the stage for rapid, confident responses in subsequent, related incidents.
#Case 2 - Deja vu
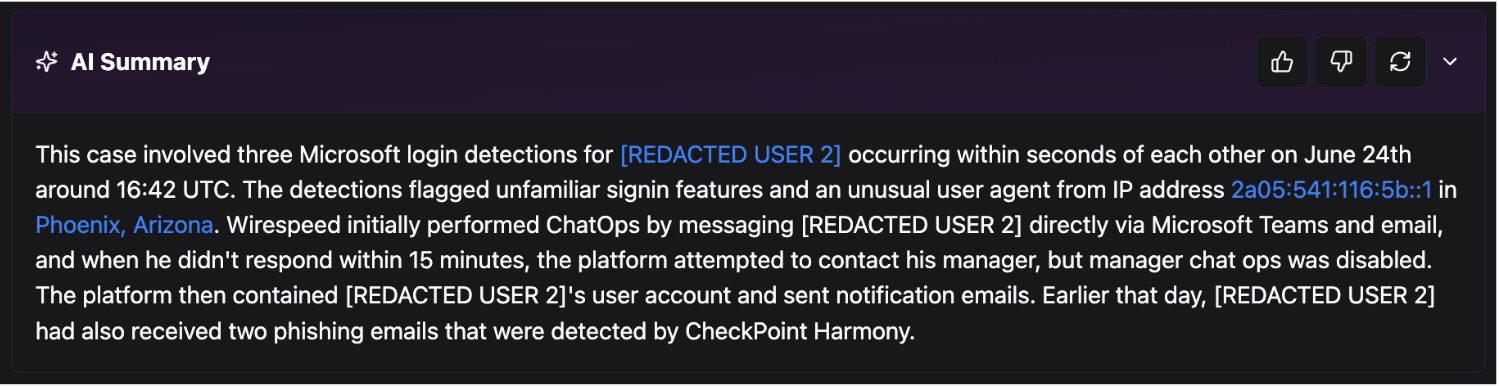
Approximately 10 hours after escalating Case 1, we escalated a similar detection for [Redacted-User-2] from [Redacted-Organization-1]. This user was targeted in what appeared to be a nearly identical phishing campaign. Instead of diving into another full case breakdown, here’s the AI-generated summary we attached to Case 2.
Note: If you’ve spent any time reading our blog, you know we’re skeptical about today’s GenAI making security decisions outright. But we do recognize its value as an augmentation tool and is why it holds a carefully scoped role on our platform.
Context:
- [Redacted-Organization-1] configured their ChatOps to wait 15 minutes for the user to respond prior to escalating to the user’s manager and restart the delay cycle.
- That “unusual user agent” our summary mentions is axios, a user agent for the javascript Axios HTTP client library, commonly present in AiTM phishing. Also, the exact same user agent from Case 1.
Here’s the kicker:
The IPs involved in Case 1 and Case 2 differed by just one hextet!
#Adjacent IP Addresses
This is where our concept of Adjacent IP Addresses shines. Here’s how it works:
- When we enrich an IP address via IPInfo, we gather its ASN, geolocation, and privacy flags (indicating if it’s associated with hosting providers, VPNs, proxies, etc.).
- We store this enriched data with the IP object in OCSF format.
- Using native enrichments, we identify IPs within a “nearby” CIDR range (/24 for IPv4 and /60 for IPv6) that share these attributes.
- If an IP matches all these criteria, we classify it as “adjacent” allowing us to infer that it shares the same disposition.
So in this example:
- The IP from Case 1 was classified as malicious.
- The IP from Case 2 (
2a05:541:116:5b::1) lies in the same /60 subnet as Case 1’s IP (2a05:541:116:5e::1). - Both share identical ASN, geolocation, and privacy flags.
- We can confidently know Case 2’s IP is malicious
- Plus, since [Redacted-Organization-1] has automated-containment configured, we immediately contain the account.
#Why this matters
Case 2 involved two 15-minute ChatOps delays — the longest pause in our otherwise lightning-fast workflow. While our automated ChatOps already far-outpaces traditional MDR/SOC response times (often by orders of magnitude), it’s still a fallback when we can’t deduce a verdict ourselves.
By constructing this “adjacent IP intelligence”, we add one more known data point into the equation and reduce threat actor dwell times to seconds instead of minutes. This is just one example of how we push the envelope on creative data enrichment to make smarter, faster security decisions.
But wait, there’s more:
#Case 3 - Herd Immunity
At Wirespeed, we believe security should be democratized: shared, transparent, and collaborative across all tenants managed under a single service provider. We’ve been of this mind since day one:
- ChatOps engages users interactively when more context is needed
- a customizable verdict framework lets each tenant tailor threat policy decisions to their unique risk appetite
- and today, we’re introducing the idea of a shared memory that echos malicious indicators across all tenants within the same service provider.
When one tenant detects malicious activity, we don’t treat it as an isolated incident. Instead, can we share that intelligence – specifically, confirmed malicious IPs – across all child tenants within the same service provider umbrella. This creates a form of herd immunity, where the knowledge gained from one tenant protects a subset of the whole ecosystem. Shared memory means faster detection (and in turn, faster containment!) of related attacks across different organizations based on trusted verdicts from sibling tenants.
Here’s where the magic happens:
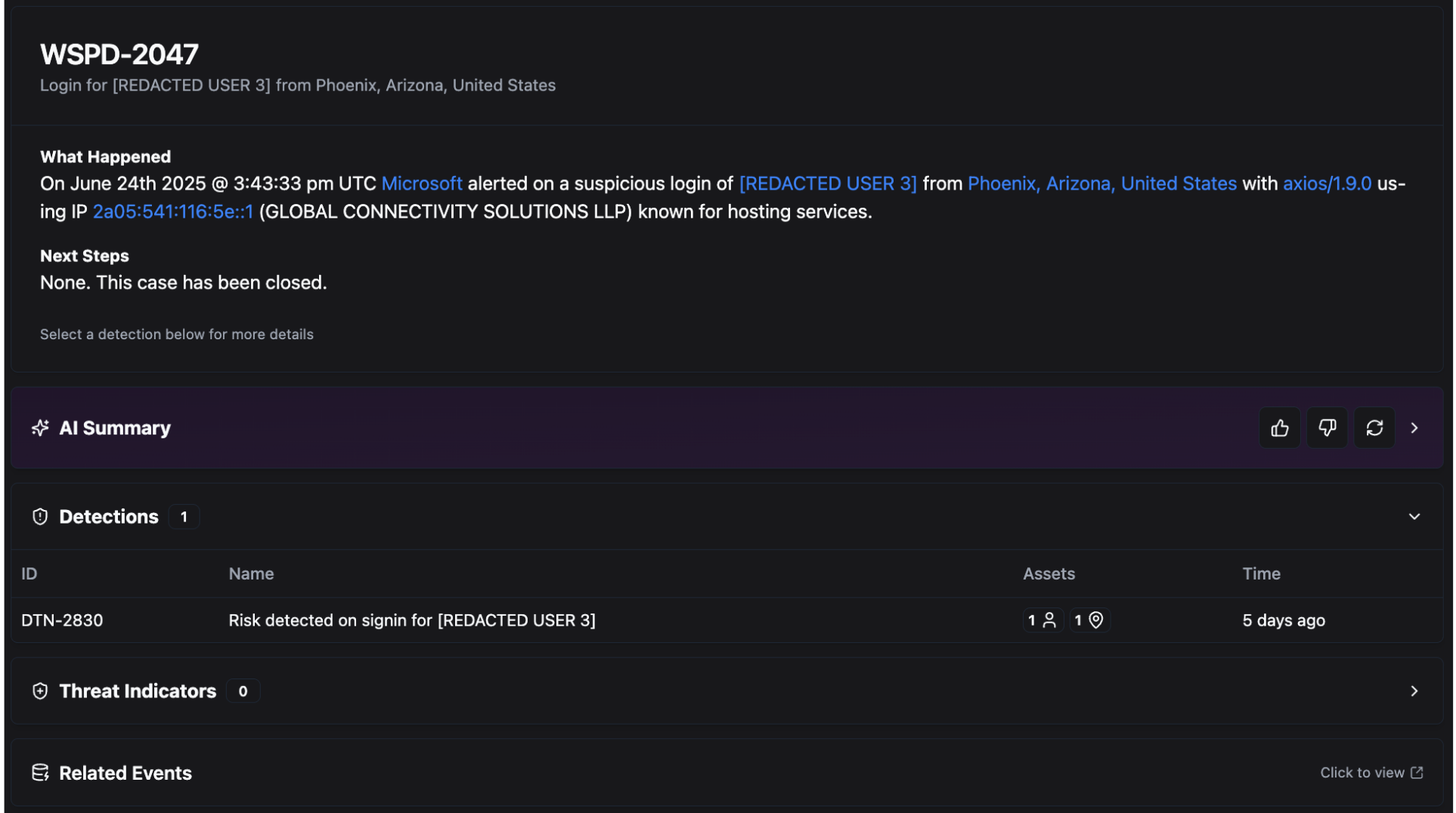
Case 3 involves a different tenant, [Redacted-Organization-2], but the same service provider and attack method. In this example, we see the same attacker IP and user agent as in the first case, but now targeting a new business about 23 hours later. With Herd Immunity, the threat can be recognized and contained almost instantly.
#Summary
| Case | IP Address | Tenant | Service Provider | Notable Features |
|---|---|---|---|---|
| 1 | 2a05:541:116:5e::1 |
Redacted-Organization-1 | same service provider | blazing fast triage, ChatOps, automated containment |
| 2 | 2a05:541:116:5b::1 |
Redacted-Organization-1 | same service provider | adjacent IP, same attack indicators, automated containment |
| 3 | 2a05:541:116:5e::1 |
Redacted-Organization-2 | same service provider | herd immunity, cross-tenant protection, fastest escalation |
With Wirespeed, businesses can be confident that their security posture is both robust and proactive, no matter which tenant is targeted. Our intelligent process and conditional logic automation ensure that every client benefits from the collective strength of the entire ecosystem.

Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.