

Tim MalcomVetter
Co-Founder / CEO
This Breach was Contained for FREE!
In today’s Success Story, the good guys won … during a Wirespeed evaluation for FREE! How fortunate was this timing?
#TL/DR;
- Bad guy took over a victim’s account
- True to our name, we triaged the detection Wirespeed-fast in seconds
- Because it was an evaluation, ChatOps & Auto-Containment were disabled
- The customer’s Tech Team responded to the escalation fast
- Bad guy had only 14 minutes of unauthorized access
- But it was long enough for the bad guy to attempt internal phishing!
#What Happened
A prospect of ours agreed to spin up a free trial of Wirespeed. In about 15 minutes’ time, we had walked them through integrating their entire Microsoft 365 stack with all the Defender for Whatever products. We pulled the previous 90 days’ worth of detections, triaged them instantly, and started building a baseline for their organization. All new tenants start off in “Test Mode” where we don’t reach out or write back to any of the customer’s environments.
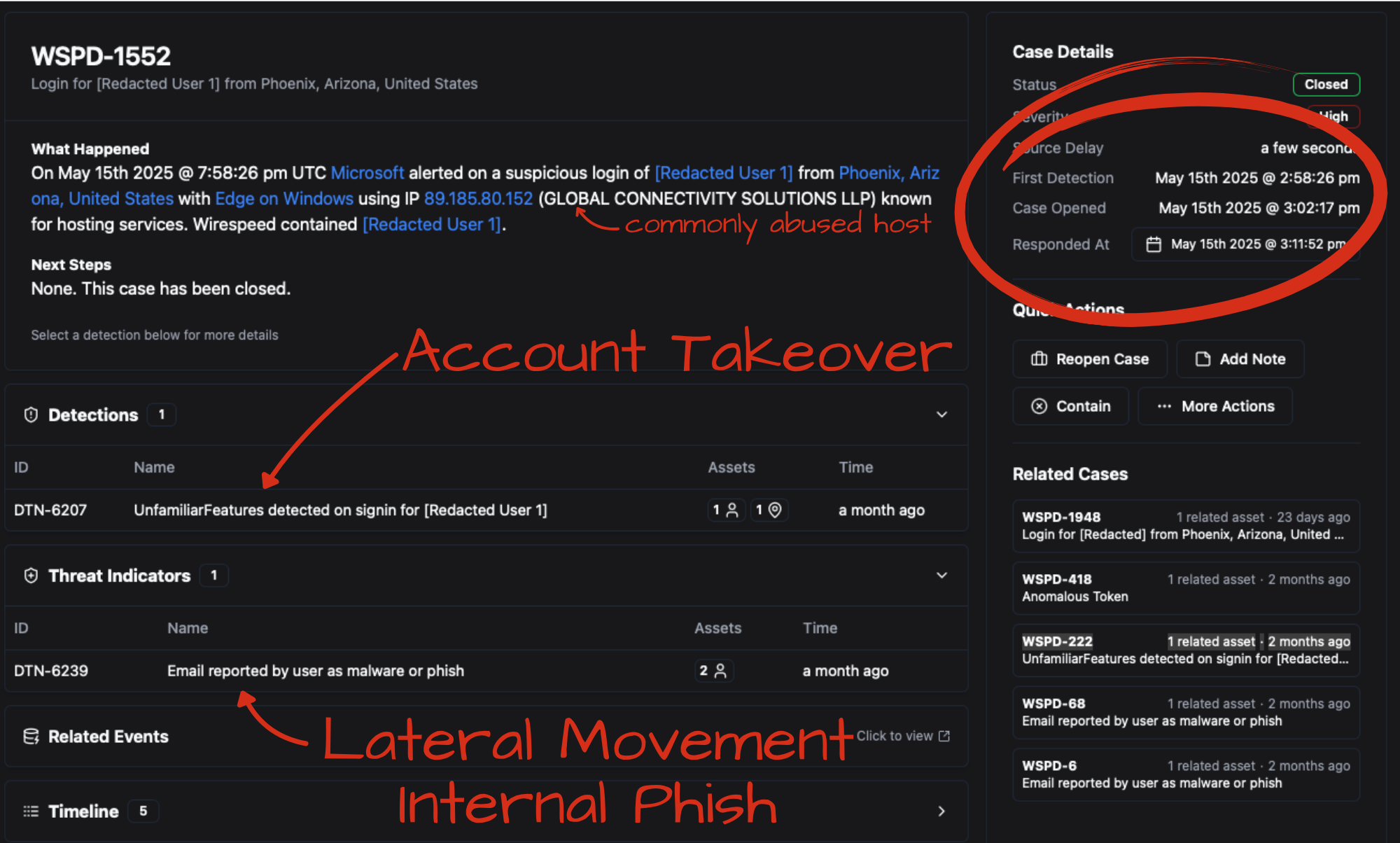
Not long into the evaluation, we received a suspicious login alert for one of their users. Very common. (We see about 3-5 identity alerts for every endpoint alert these days, and most companies and their outsourced SOCs do very little if anything at all with them.)
What transpired was an interesting 14 minutes, starting as a suspicious login, but quickly recognized as hostile, because we have seen that particular ASN and user agent combination used frequently from adjacent IP addresses against a couple of our other clients.
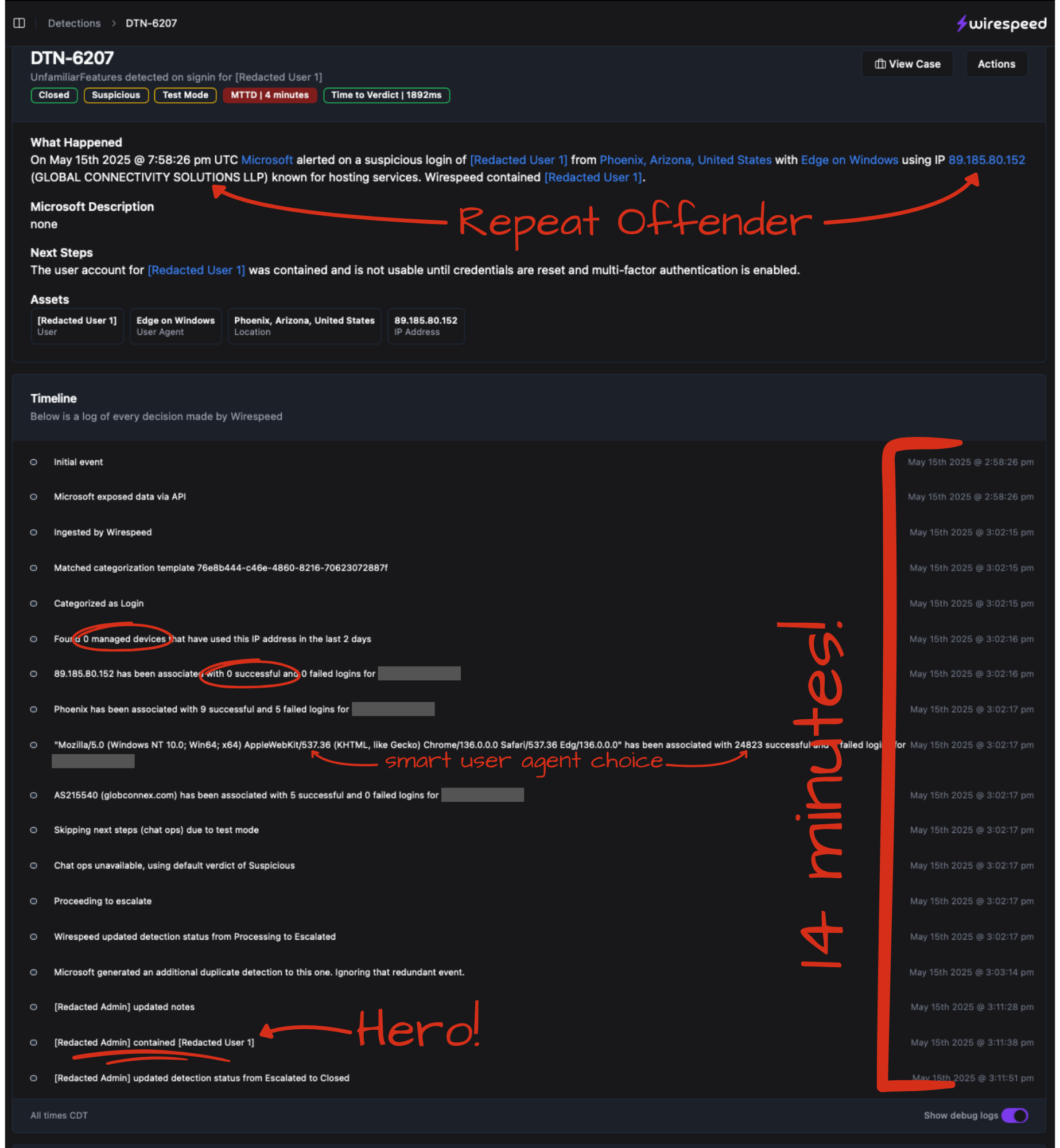
As you can see above, the login clearly didn’t come from a known good place. No managed devices, an unfamiliar IP, an ASN network block that has only been hostile, but the attacker chose a very common user agent to appear legitimate.
Since the customer was in an evaluation, they didn’t turn on ChatOps, where we would have pinged the user over Slack, Teams, Email, or SMS to confirm the login activity automatically.
They also didn’t turn on automatic containment—which we allow to be set per category, i.e. just identity cases where suspicious logins happen, and only for your general workforce (not your exec team VIPs or your non-human service accounts).
Nevertheless, our client’s technical team did receive our near instantaneous escalation from us after our 2 seconds (that was slow for us!) verdict time and after an approximately 2 minute ingestion delay (typical) upstream from us on the Microsoft side. About 14 minutes after the initial rogue login, our client’s technical team used Wirespeed to contain the user, i.e. disabling the account and killing all sessions.
Then this happened:
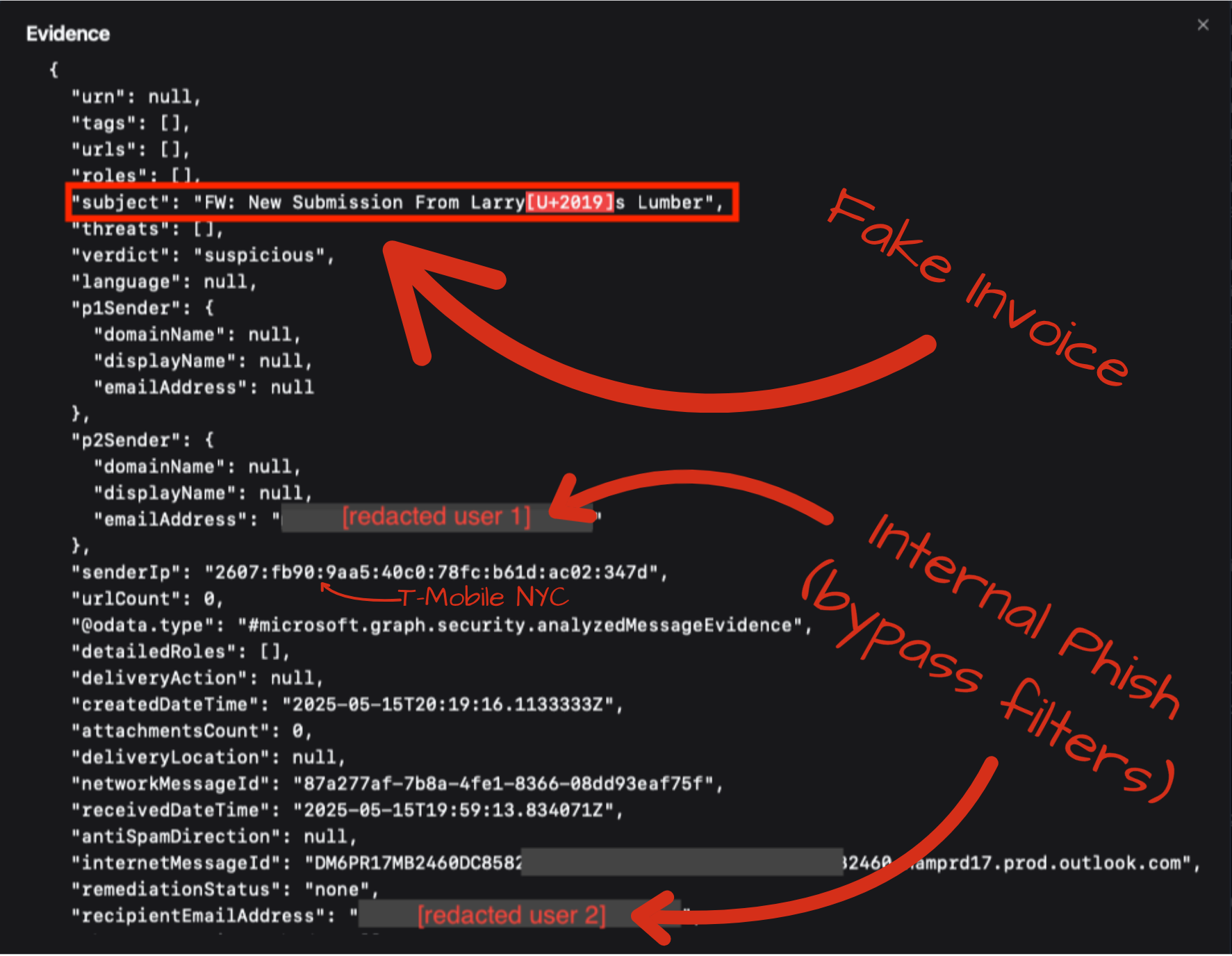
A second user inside the company reported receiving a phishing email … sent from the first user whose account was taken over!
#We see this tactic frequently
When the first user account’s access permissions aren’t good enough for the attacker to reach his goals, abusing that user account to send phishing emails “inside” directly to another teammate can be a lucrative option. It bypasses the email filters that check for spam and phishing, because it’s user-to-user. Most phishing checks only happen at the email gateway, as emails come into the organization from the outside.
Fortunately, this fake invoice from “Larry’s Lumber” didn’t resonate with its victim, the second user, and the attacker’s access died right there. Had this second user fallen for this internally-sent phish, the attacker would have had a second foothold, presumably closer to his goals of either BEC (business email compromise often leading to wire transaction fraud) or possibly ransomware. Given this target wasn’t technical, it was likely the former (BEC - wire fraud).
Since most organizations struggle to detect, let alone respond, to identity alerts, an attacker who can use the first account takeover to pivot into a second user account via internal phishing is likely to persist inside the victim organization undetected all the way until they achieve material impact (i.e. wire fraud or ransomware), but not with us! We investigate EVERY single suspicious login alerts thoroughly and automatically, even the benign ones.
#Stitching all the data together
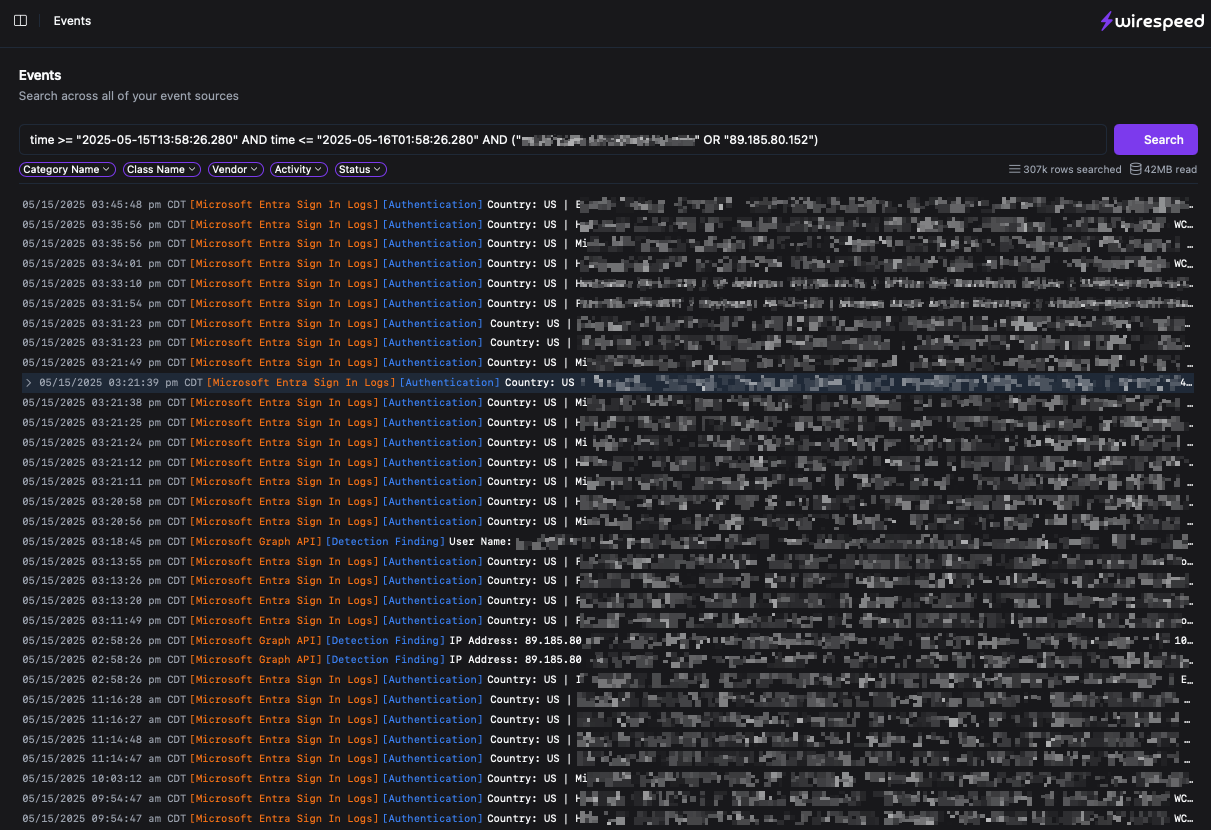
We captured the attempted phish and linked it to the rogue login case as a correlated “threat indicator” (see above), rounding out the complete story of activities, all triaged, enriched, and correlated without a single human intervening!
Also fortunately, Wirespeed stores all of the related events in our super fast datalake, powered by Clickhouse, so it’s easy to quickly verify all of the additional activity to make sure nothing else was accessed:
#Long Story Short
This could have easily led to material impact, but it didn’t. What was a quick 14 minute response time, would have been 4 minutes (including time to wait on the victim user to respond to ChatOps, on average, based on our typical in-production clients) if ChatOps and automatic containment were enabled.

Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.