Tim MalcomVetter
Co-Founder / CEO
This is part of a blog series tackling common problems in traditional MDR and outsourced/Managed SOC Service Providers (MSSPs).
My MDR Doesn’t… Tell me Mimikatz was Contained
Mimikatz is an open source tool released in 2012 and designed to extract copies of plaintext passwords stored in memory in the Microsoft Windows LSASS security process. The intent of this article isn’t so much about Mimikatz, but the entire category of malware that is used in the Late Stages of an Attack.
Wirespeed refers to Late Stage Tools as the general over-arching category of tools like Mimikatz. These are all tools that are used by attackers (including Red Teams) to perform lateral movement, privilege escalation, remote persistence, and achieve the attacker’s objective impact, such as getting king-of-the-hill admin access to deploy ransomware.
Contained in this context means an EDR (Endpoint Detection and Response) tool alerted on the presence of the malware, blocked it from executing, perhaps even quarantining or deleting it.
#Do these alerts even matter?
Oh, they certainly matter.
These kinds of alerts are indicators of the presence of an attacker. Tools like Mimikatz don’t just end up on an endpoint device out of the blue. You can’t just get a drive-by download from a random website that has been compromised to serve up malware. The purpose of First Stage Malware is to get a comfortable execution context—often free of observability from security controls—so the attacker can start loading later stage malware tools like Mimikatz to gain more access towards their objective.
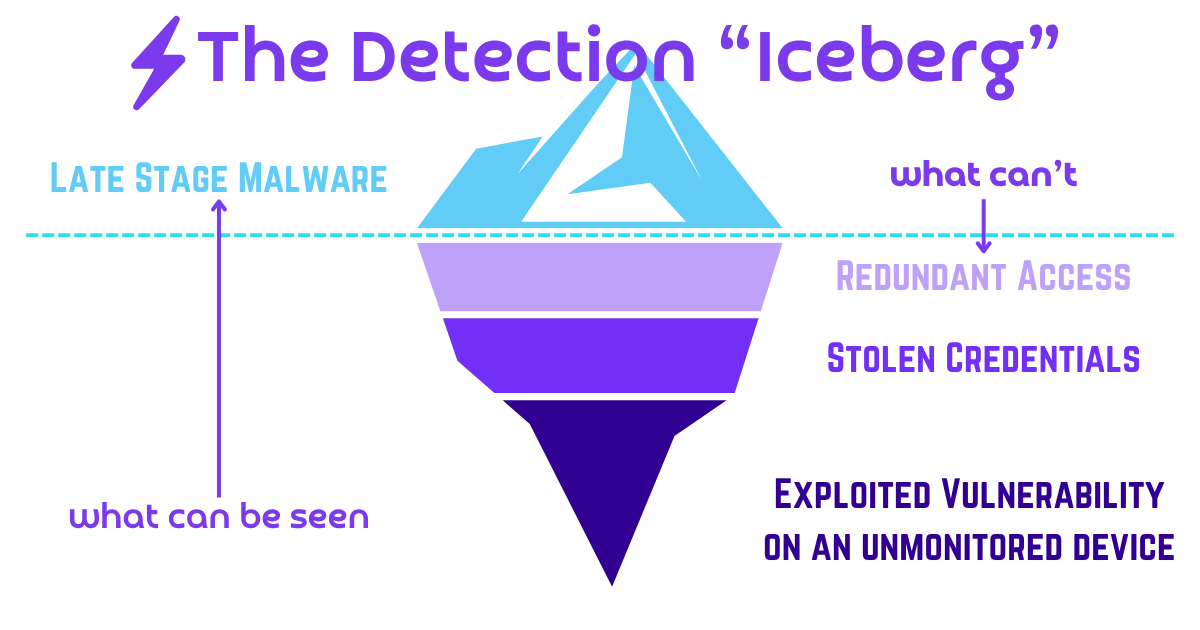
So if all you see is the mitigation of a Late Stage Tool then you’re just seeing the part of the Detection Iceberg that is above the visible water line:
An alert for First Stage Malware getting blocked is ok to dismiss, although we would recommend reviewing them periodically in aggregate to get a feel for the overall security posture of your organization and its cyber-hygiene behaviors. If your MDR provider doesn’t alert on First Stage Malware they’re saving you time and keeping your attention focused on more important things. That’s certainly important to do.
As a Red Teamer, if I had gained access to a network that had detection controls that generated alerts about my Late Stage Tools, but then simply gobbled them up, deleted them, or auto-closed them, then it’s not a Chess Match against a sentient opponent. It’s simply a matter of time before the attacker can outwit the detection controls. In the case of Late Stage malware, not responding with the full force of Incident Response is a gift to the attacker, allowing them time to simply repackage or restage their tool to bypass detection and get into an execution context, where the attacker can then gain the access they’re after.
If your MDR provider won’t tell you about how a Late Stage Tool is blocked on one of your endpoints, this is your security program:

How Wirespeed is Different
First, Wirespeed brings a Red Team background to our approach to MDR, so we maintain lists of the kinds of tools we used as Red Teamers: privilege escalation, lateral movement, interactive C2, etc., and we include families of ransomware and closed source criminal C2 families as well. We discover their presence through indicators in source telemetry you send to us as well as from our File Reputation Enrichment Providers.
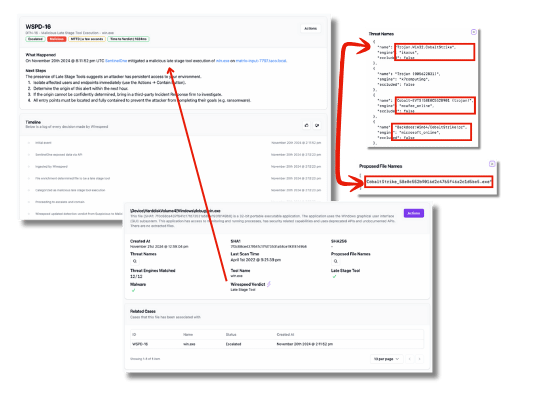
Here is an example of a Sentinel One alert that, without our added context, would appear like mundane malware:
Since Sentinel One mitigated (blocked/quarantined) it, an average MSSP/MDR may simply close the case and not tell you about it. In this Wirespeed case, however, we informed the security team to do the following four things:
- Assume the user’s credentials are also compromised and rotate them, killing all sessions (we do that for you, if you let us).
- Determine the origin of the alert
- Without knowing the origin, you must consider this a live breach and bring in a competent Incident Response team.
- Ensure all of the entry points are fully contained
We do this because of the Detection Iceberg. We assume there are layers under the water we cannot see, such as a compromised device on the network edge facing the internet or a user missing MFA. The sources need to be found, or the bad guy simply walk right back in.
We do our best not to bother you, but if we see a detection like this, we’re certainly going to do our best to wake you up!
#Run us Head to Head
We’re ready to run head-to-head against your current MDR provider, because you deserve to have an MDR that thinks like the adversary to outsmart them. Alerts like this should NEVER be ignored; they may be the only signal you receive before material impact to your organization.
It takes just a couple minutes to start a FREE Trial, where we will ingest your prior 90 days of alerts and show you cases where we would have reached out to your victim users. Did your MDR provider even tell you about any of them? How about all of them? After that, you’re welcome to integrate with Slack, Teams, or just email, and we’ll watch you for the next 14 days for FREE, reaching out to your users on your behalf. We’ll even help you with a rollout communication plan to inform your workforce that they may be asked about their activity to protect your organization. Quick, Easy, Painless … and Secure.

Want to know more about Wirespeed? Follow us on LinkedIn / X or start a FREE TRIAL today.