
Tim MalcomVetter
Co-Founder / CEO
Best File Reputation Vendors of 2025
#What is file reputation?
File reputation vendors take the cryptographic hash of a file (and in some cases the file itself) and analyze it to assess if it is a security concern or not. The most obvious is checking Windows portable executable (.exe and .dll) files for signs of malice, but many other files, like Mac/Linux executables and common document formats, often need to be assessed as well.
#Why are we writing this?
We’re writing this because no such guide existed when we went on a six week deep dive into this space looking for a solution for our Wirespeed Automated MDR service. Since we did the analysis—and we have no financial incentives tied to any of these companies (we think we are being pretty fair to all of them, all things considered), we thought we’d share back with the cybersecurity community. To spell it out: not a single vendor gave us a cent for this (and we pay to license the one we chose).
#The Competitors:
- VirusTotal by Google
- MetaDefender by OPSWAT
- Stairwell
- Sophos Labs Intellix API
- OpenText BrightCloud (WebRoot AV)
- Broadcom Symantec
- Spectra Intelligence by ReversingLabs
I don’t want to read this, just take me to the winner!
Or jump down to learn how Wirespeed uses File Reputation.

#VirusTotal by Google
URL: https://www.virustotal.com
#Pros:
- The Kleenex of File Reputation, everyone knows what it is (and probably none of the competitors)
- Great metadata, including publisher source for some files
- Lots of community uploads, perhaps the largest dataset (claim: ~50B files, ~1.8M daily)
- Windows, Mac, *nix
- Free for personal use (limited API automation)
- Can download original files with only the hash
#Cons:
- Concerns over licensing availability with GTI (Google Threat Intelligence)
- You may have to license it in such a way that you can’t tell anyone you’re using it
- $$$ Very expensive
VirusTotal basically invented the concept of multiscanning with OPSWAT MetaDefender coming shortly after. Ask anyone in cybersecurity about the concept of checking file hashes for comparative malware engine results, 99.9% of them will mention VirusTotal, many not realizing there are alternatives. VirusTotal has definitely achieved “Kleenex” status in brand recognition, dominating the category. The community support has been historically good and the web UI is still probably the best of any of the tools we tested (but we’re really after the data and API integrations, so the UI is only an honorable mention for us).
The darker side is that VT appears to have taken a backseat after the Mandiant acquisition by Google. Many friends of ours, both at enterprises and MSSPs, have indicated that either their VT prices have gone way up, or they’ve been told VT is no longer for sale the same way it was in the past, being replaced in favor of GTI (Google Threat Intelligence), which bundles in Mandiant Threat Reports, Mandiant’s ASM (Attack Surface Management), dark web and brand reputation monitoring, and more. This may be a way for Google to try to monetize the Mandiant acquisition; we’re not sure. We do know, though, that VT is still available for purchase by “OEMs” (what they refer MDRs/MSSPs as), but we had to fill out the “please contact me, sales team!” form a few times to get a human to respond (and that’s even with having friends at Google).
Another unusual aspect of VT pricing for “OEMs” (MDRs/MSSPs and other security vendors) is that the price goes up as you expose more of the VT result data to customers. If customers can directly interact with VT through your solution, then your price goes up. If customers can see more results, reports, and other metadata, your price goes up. If your customers are aware you use VT under the hood, your price goes up. (That last one is a head scratcher for me, because if I ran VT I would want the free advertising of my brand in every downstream vendor’s solution.)

#MetaDefender by OPSWAT
#Pros:
- Nice to see a VT competitor with a Community Edition
- Pretty good repository of files and AV engines in the free/community version
- Decent commercial pricing (which is different from “OEM pricing”)
- Windows, Mac, *nix
#Cons:
- Web UI is a little clunky sometimes (blocking search elements, annoying login UX)
- OEM (MSSP/MDR) has less engines than Commercial which has less engines than Community
- OEM (MSSP/MDR) pricing is not nearly as appealing as commercial pricing
- Overall less engines than VT
- About 1B files available in the OEM/Commercial licensing model
MetaDefender is probably a tool you didn’t even know existed, if you’ve used VT in the past. OPSWAT’s story is that the company developed security solutions for on-prem, air-gapped networks of critical infrastructure, like nuclear power plants. One such request from those customers was the ability to inspect media that was “sneakernetted” into the air-gapped network, and scan for signs of malware, especially post-Stuxnet.
MetaDefender (or as we started calling it: “MetaD”) has a free community version that certainly only receives a fraction of the traffic that the VT community version gets. It’s dark-mode themed, fairly clean, albeit there is some weird UX-ness with the search bar, especially on mobile devices, and especially if you log in, as the sessions time out frequently and the auth experience isn’t the best (but isn’t the worst), it’s just “meh,” which is what I’d probably say to describe the solution in general.
MetaD has a number of engines, around 30 something, in the community version, compared to VT’s 70 something, but don’t let that make you think it’s less than half the value of VT–it’s clearly more valuable than that. The quantity of engines certainly reminds us that “more isn’t always better,” and I started looking sideways with a critical eye at some of the engines on both VT and MetaD. There are about 10 engines, give or take, that matter to us. The rest are superfluous.
One of the big downsides is OPSWAT doesn’t have the same agreements with the engine vendors that Google has, so there are more engines in the free community edition than you can buy, and of course, it’s against the ToS to use the free version in any meaningful way, besides interactively using it to deal with threats in a non-commercial way. For big shops, like MDRs and MSSPs, you’ll be funneled into the OEM sales division, where the limits are more severe and there are even fewer engines available to you (around ~10 and not the 10 we wanted to see), at an even higher price point.

#Stairwell
#Pros:
- Very interesting approach to collecting and analyzing executable files
- Cross Platform (Windows, Mac, Linux support)
- Rich analytics UI
- Capturing ~1M files daily from enterprises, along with prevalence data
- Their API schema matches the VirusTotal’s API, making it a virtual drop-in replacement
#Cons:
- The collection is new, so the dataset is not nearly as extensive as the others
Stairwell is an up and coming solution that I expect may dominate in this space … eventually. The Stairwell team takes a novel approach to tracking and performing surgical analysis on every binary that touches a disk in an enterprise. Frankly, they can do things others on here can’t, like historical analysis based on chunks of a binary, and telling you how many managed enterprise endpoints have a copy of a given file (“prevalence”), which by itself is actionable intelligence. It’s fascinating for sure. The founder, Mike Wiacek, is ex-Google, former founder of what is now Google Cloud SecOps (but will always be either Chronicle or Backstory to me) and the approach shows: both Chronicle and Stairwell collect as much data as they can, keep it for it as long as they can, analyzing it the most novel, fastest way they can.
Stairwell only recently added the ability to consume results from their “corpus” (latin for “body”) of files and their API has a schema nearly identical (coincidentally) to VT’s, for those looking for a new home given Google’s uncertain approach to how they want to handle that product’s licensing going forward. Stairwell currently consumes about 1M files, give or take, daily, from sensors on endpoints across the largest enterprises in the world, so the data is very well-managed. That said, if you need to do file reputation analysis of files that smaller segment companies use, this may not be the dataset for you, today. I do think it will be one day, though.

#Sophos Labs Intellix API
URL: https://api.labs.sophos.com/doc/
#Pros:
- Easiest to buy (AWS consumption billing)
- Cheapest $0.002 per API file hash call
- Decades long, solid reputation as an AV vendor
- Supports archive (e.g. zip) files
#Cons:
- Dataset is limited, missing many files
- No Mac/Linux support
- Threat names are basically non-existent
- SHA-256 only
After struggling to navigate Google’s lack of motivation to sell VT, we turned towards each of the best AV engines present on VT, hoping some would sell access directly to their own file hash results. One of the first we found was Sophos Labs Intellix, which seemed super promising at first. For one thing, we could spin up and test it ourselves without talking to a Sales Rep (something you’ll note we do at Wirespeed, so it’s a valuable approach to us!), namely because Sophos meters the consumption of their API through AWS, so you can consume it, just like any other AWS service. The pricing is also extremely affordable: $0.002 per successful API call. That’s right: one-fifth of a copper penny per lookup.
The downsides to this API, besides only being single engine, is that it’s lacking the more robust metadata we’ve come to expect from solutions like VT. The verdict scores are an integer 0 to 100, with their own weird rubric, which is fine once we’ve got code wrapping the service, but confusing at first. There’s virtually no metadata for files that are known good, and the known bad files’ threat names were typically non-expressive, which didn’t meet our use case. The dataset seems pretty good, but there were quite a few files in our testing that were not present in their records that are present in some of the other services. We really wanted this one to work out, due to its price and ease of testing/buying.

#OpenText BrightCloud (WebRoot AV)
UR: https://www.brightcloud.com/threat-intelligence-services/file-reputation
#Pros:
- Really impressive coverage, the best we saw for a single engine and better than many multi-engines
- Large deployment of WebRoot AV on consumer devices actually diversifies the dataset quite a bit!
- Very reasonable and scalable pricing tiers based on consumption
#Cons:
- No Mac/Linux files
- Only Windows PE files (executables and DLLs)
- No SHA-1, only MD5 and SHA-256
- Threat names aren’t always expressive (e.g. “W32.Trojan.Genkd” vs. “W32.Trojan.Mimikatz”)
- Single engine (all eggs, one basket)
If you’re like me, with twenty-something years in cybersecurity, you probably haven’t tracked OpenText as a company. In fact, my first association with that brand, nearly twenty years ago, was for a document management system that competed against an early version Microsoft SharePoint, completely outside any indication they were even aware of cybersecurity. That said, the company (OpenText) acquired a company (BrightCloud) which acquired a company (WebRoot) which has had an antivirus product for many, many years.
Also, if you’re like me, you’ve probably heard of WebRoot, but haven’t had much direct experience with it. Despite that, WebRoot AV has become “the little engine that could” to us, and we were quickly won over by it. Why? Because its dataset was very impressive. WebRoot AV has been installed on millions and millions of consumer grade PCs for decades, which are exactly the kinds of systems that have had the worst and most varied malware dumped on them. One thing that Webroot made us appreciate is the overlap in the types of executables present on SMB and mid-market endpoints and consumer PCs, which are often quite different from enterprise systems, which are more heavily regulated, keeping sloppy software out.
One example was a banking application that only lives on a single endpoint at one of our customers. The enterprise grade EDR agent installed on this mid-market company did not like that this banking application uses the same Windows APIs that keystroke loggers use, only it’s defensively to prevent malware from keystroke logging in this case. When a scary behavioral alert like this pops up, it’s important to be able to instantly de-conflict by getting the file reputation of the executable by its hash. What we found is that virtually none of these providers on this list had this hash in its dataset, but WebRoot (OpenText) did, and that really piqued our interest. A month or so later when the same endpoint generated a new alert of an updated version of the same banking application, which now had a new hash, we were very impressed to see WebRoot had it, and they had scanned it the same day the alert fired, which makes me think someone else out there also processed an alert from that same banking app on the day the update rolled out.
Metadata from the API responses are also just enough to be helpful. You get a nice clear Good, Bad, or Unknown result, unlike many of the others that like to get wishy-washy in the middle with a “we’re not sure, but we think this is suspicious, but not suspicious enough to call it malicious, so we’re going to outsource the analysis back to you, even though you’re paying us to analyze this file.” The threat names aren’t always the best, sometimes they’re just categories, sometimes they’re expressive, and good files don’t get nearly as much metadata as you’d see in VT.
Pricing tiers are reasonable for OpenText, close to some of the other multi-scanning vendors, which likely indicates it’s a bit too high, especially for a single engine vs. multi-scanner approach, but if we’ve learned anything through this analysis, it’s the dataset that matters so much more than the engine count, so the pricing wasn’t a big problem for us at all (especially compared to VirusTotal).
The issues for us are centered around WebRoot’s limitation to only Windows PE files, the inability to handle anything beyond .exe and .dll files specifically, not even in compressed archives (e.g. .zip files), and Mac/Linux are a no-go as WebRoot has never been built to run on anything but Windows.
One other interesting peculiarity is that the dataset clearly began in the pre-SHA hash family days. MD5 is supported and predominant. SHA-1 was skipped in favor of SHA-256. Why does this matter? Because, annoyingly, SentinelOne doesn’t capture SHA-256 hashes by default. Ask anyone with S1 experience and they’ll likely tell you to simply “upload the SHA-1 hashes to VT to get the SHA-256,” as if that helps this situation! If you are limited to SHA-256 and Windows PE files, this should automatically be a finalist for you! Yes, you can enable SentinelOne to collect SHA-256 hashes, but in our experience, that can be as simple as clicking a button or a debate with the partner who sold you S1 who also doesn’t understand why you might care about SHA-256 (“just upload to VT”), but they are the gatekeeper of your configuration. This is NOT something we want to ever deal with (again), so lack of SHA-1 support was unfortunately a deal-breaker in itself!

#Broadcom Symantec File Reputation Service
#Pros:
- Symantec AV has decades of file scanning, so in theory a dataset should be extensive
#Cons:
- Didn’t find a way to evaluate or talk to anyone about purchasing a subscription
- Product lost in the Broadcom acquisition
I must admit I’ve never been a fan of Symantec. Never. Not even back in the days when AV was pretty much McAfee vs Symantec. But, this analysis project has definitely proven that’s all about the dataset, not the engines themselves, so we wanted to consider all options. According to Google, Symantec does in fact have a File Reputation Service, but it’s lost in the cracks of the Broadcom acquisition of Symantec and we gave up.
#Spectra Intelligence by ReversingLabs
URL: https://www.reversinglabs.com/products/spectra-intelligence
#Pros:
- The largest data set (40B files), second only to VT (and that may be disputable)
- Support for 4,000+ file formats, including Windows, Mac, Linux, and compressed archives
- Super detailed analysis that a reverse engineer would love (lives up to their name)
- 20 something scanning engines, all solid choices (but sadly doesn’t include our new fav: WebRoot)
- More hash formats than you’ll probably ever care about
- Can download any file hash match, just like VT
- Supports uploading your own files for analysis, including with privacy
- One of the best performing APIs we tested with responses often under 200ms, which is amazing given all the data it’s serializing to JSON in some responses
#Cons:
- Little annoyances, like file hash verdict is one API call, metadata details is a second API call
- There were some misses in the dataset that only OpenText and VT had, but no dataset is perfect
ReversingLabs’ solution wasn’t one we discovered right away. In fact, someone needs to go edit the Multiscanning Wikipedia page to make sure ReversingLabs is included, because they have arguably the second or third highest count of engines out of all the solutions on that list. Unlike the engines in OPSWAT’s MetaDefender, there are no real fillers in the list (except maybe ClamAV).
ReversingLabs (RL) and Stairwell both share their own deep file analysis data in their APIs, which set them both apart from the other options. RL’s responses look like, well, a Reverse Engineer compiled the results. You can see metadata about the type of file, headers, formats, sections of the binary, libraries that are imported, functions and features that are called, and there’s even a robust narrative description of the executable that’s available in the API. All of that is in addition to the multi-engine scan results, which include their own very expressive threat names (if that matters to you, like it does to us). They’ll even tell you every single time they ever scanned a file in their repository, which engines they used, the versions of the engines, and the individual results. And they pull all of that history together with impressive response times in their API (things like this matter to a company called “Wirespeed”).
One thing this project taught us is that the quantity of files not only matters, but also the sprawl of the types of files in the repository. RL has a much wider variety of types of files it supports when compared to OpenText, one of our favorites, but OpenText’s depth in the file types it does support means they had more hits that RL didn’t have. Most of these vendors allow you to upload files (if you have them) to the API to be statically analyzed and added to their repositories for future lookups, so your choice of solution may come down to which is more painful to you: fetching and submitting an unknown file for analysis or not having coverage for more file type sprawl.
Another thing we really like about ReversingLabs is the role of Spectra Intelligence in the company’s overall mission. There’s something to be said about buying a flagship or strategic product from a vendor, vs. an ancillary side project. Since Google’s primary motivation is to sell more Google Cloud consumption and a strong secondary motivation for them is to monetize their acquisition of Mandiant, VirusTotal is certainly not a primary or flagship product to them. RL, on the other hand, is a smaller, growth stage cybersecurity company who has pivoted towards Supply Chain security, which Spectra Intelligence clearly enables, making it more strategic of a product for them (even if the API consumption is just a side way to monetize the underlying tech).
#Winners
#Best Free (Non-Commercial, Limited) Use
Winner: VirusTotal
VirusTotal is free for non-commercial, low-volume use. This is how it became the “Kleenex” of the file reputation category. OPSWAT also has a free community edition, but the UI/UX isn’t the best. We would really, really like to see ReversingLabs release a non-commercial community web UI!
#Best Low Budget Option
Winner: Sophos
Sophos Labs Intellix API, at one-fifth of a cent per lookup, wins the best budget Windows-only option, hands down, provided you only want to know if a PE (.exe and .dll) file is malicious with a modicum of accuracy (call it maybe 75% or so due to the missing files) and don’t need meaningful threat names or other metadata.
#Best for Windows Only
Winner: OpenText (WebRoot)
OpenText’s BrightCloud service based on WebRoot AV surprised us tremendously. What it has in limitations with Windows PE files only, no archive files, and no SHA-1 support, it makes up amazingly in the depth of its dataset and reasonable pricing. Definitely worth a look for Windows Only.
#The One to Watch
Winner: Stairwell
As their “corpus” of files grows, Stairwell will become a contender for the top spot, and they’ll certainly innovate more than Google while reaching that position. In fact, it will be fun to watch Stairwell and ReversingLabs compete in this space, because all of us will benefit.
#Overall Best File Reputation Vendor in 2025
OVERALL WINNER: ReversingLabs
We chose ReversingLabs. If your budget is very large, choosing Google’s VirusTotal is a safe choice, but if you’d like to see more innovation in this space and want even deeper analysis, choose RL for all the reasons we provided above and for the examples of how we use it at Wirespeed below.
Using File Reputation
#How Wirespeed Uses File Reputation
All Security Operations Centers (SOCs) need the ability to take alerts, enrich them, and make smart decisions. Wirespeed MDR adds the additional requirement of being able to process all of our decisions programmatically. We need good data that a repeatable algorithm can follow–the same algorithm that SOC analysts use mentally, just ours is literally codified.
#Dismissing False Positives
It’s no secret that detection vendors are liability driven, meaning they err on the side of over-alerting rather than under-alerting, so that customers can never say the product was at fault and missed an actual intrusion that resulted in damages.
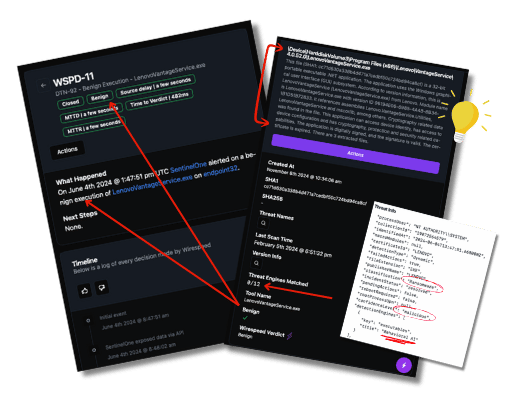
This first example is a real case that we worked with our Reversing Labs integration. You can see from the raw JSON that SentinelOne categorized this as Ransomware with a confidence of malicious. That alone is enough to give a SOC analyst a stressful day! We bumped the SHA-1 hash up against the ReversingLabs’ API and could confidently use their third-party opinion to dismiss the alert. We can clearly see this is a legit application from Lenovo. Best part, we were able to process the entire alert with all of our enrichments and decisions in just under a half second (482ms) and our customer could stay focused on things that mattered that day–not chasing fake ransomware! Also, because everything we do is completely transparent, our customer can see our case, see why we dismissed it, and if they need receipts, they even have the nice narrative “story” about the executable from ReversingLabs as an extra touch.
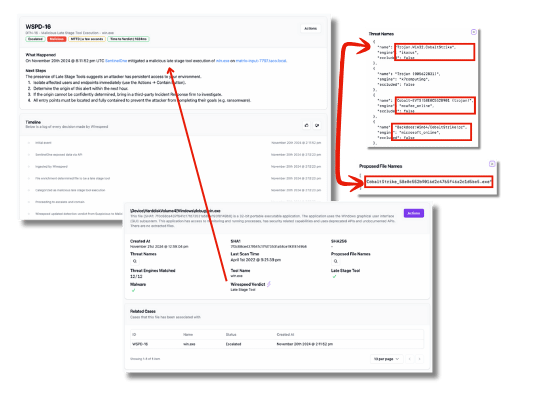
#Identifying Late Stage Malware
In this second example, SentinelOne alerted on malware behavior, but Wirespeed is able to confidently identify the malware as Cobalt Strike. Wirespeed has its own list of “Late Stage Tools” including C2, ransomware families, and other privilege escalation, lateral movement, and red team tools, which we regex against EDR alerts and ReversingLabs’ analysis. Since these types of malware don’t suddenly exist on an endpoint (an attacker must stage them after getting access), we can infer an attacker has gotten quite far down the attack “kill chain.” In this case, it does not matter than the EDR blocked the malware, because the mere presence of this kind of malware indicates an attacker likely has a persistent means of access beyond what the alert says. An attacker with persistent access could simply re-package or stage this Late Stage Tool in a different way to get it past the EDR. We treat these cases with the highest level of severity and urgency, automatically isolating endpoints from the network and rotating credentials of affected users (if our customer opts for our recommended minimum auto-containment settings).
#De-conflicting Legitimate Software
In this final example set, Microsoft Defender for Endpoint (DFE) alerted on suspicious runtime behaviors: monitoring keystrokes and hiding the UI components of a process. DFE alerted repeatedly on the first one, which ReversingLabs helped identify as a legitimate third party administrative toolset, which we can then validate is being executed by a valid administrator in an expected way. Keystroke monitoring alerts are scary, but we can de-conflict the API calls of the administrative tool, because ReversingLabs provides us with every DLL that is imported into the Windows PE file and every function endpoint that is being captured (those details are not pictured in the UI below, but are available to us programmatically for making decisions). The second screenshot in this set depicts a legitimate banking application, which was not a known file hash for most of the competitors listed above when we performed our comparison tests. Because the bank who publishes the application is smaller with a much reduced reach of customers and lower install-base, big enterprise tools were often not familiar with it, but our mid-market customers need fast, reliable verdicts about its execution.
#Summary
Going into 2025, there are many more file reputation vendors out there and since adversaries are getting faster, it’s important to pick good intelligence enrichment layers to make fast decisions, or pick an MDR partner like Wirespeed who can do it all for you. Stay safe!
Want to see what Wirespeed is all about? Follow us on LinkedIn / X or Start a FREE TRIAL in 5 minutes and put us head-to-head against whatever you use for detection & response.