

Tim MalcomVetter
Co-Founder / CEO
Adversaries are Speeding Up
We are currently living in the final days of an era in which adversaries are still taking hours to days, on average, to accomplish their objectives. We’re approaching breaches best measured in minutes. Maybe even seconds.
#The Current Breach Landscape
We don’t have excellent (public) detailed data on breaches; we mostly have scattered anecdotes and private back-channel discussions, with a few gems here and there. There are a few stories in which adversaries achieve “material impact” (to use the SEC inspired buzz word of the month) in minutes, but most take longer. There are also breaches which took on a larger than life misunderstanding, such as the Equifax breach. (Ask your cybersecurity friends about that one and they’ll likely mention a missing, ancient Apache Struts patch, but fail to mention the months of adversary dwell time, in which there were likely dozens of internal detection opportunities that were missed or ignored.)
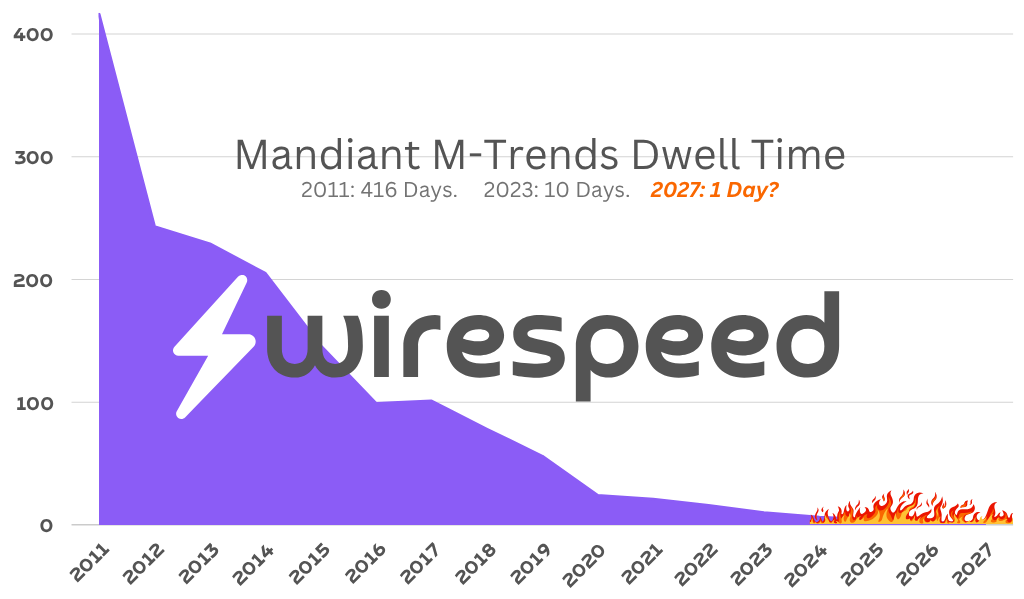
The closest, public data series we have is the Mandiant M-Trends Dwell Time published in their annual reports since 2011. A few points on this:
-
“Dwell Time” means the time from when an adversary gains unauthorized access to the time they’re detected (not contained)
-
This data is the average. Mandiant worked breaches with very short dwell times and some with super long dwell times measured in days/months where the defenders left the light on, but were asleep at the wheel. The cases with longer dwell times obviously skew the overall average.
-
Ransomware tactics have shortened dwell times considerably since adversaries have to notify their victims that they’ve been ransomed (i.e. presumably the victims otherwise would not be aware of the intrusion).
Number 3 is the reason why the dwell time metric is so important: to survive an intrusion from a ransomware actor, an organization has to detect and respond faster than they can dominate the environment. In fact, for the past 3 years of Mandiant’s M-Trends data, the majority of “detections” were “external,” including ransom notes.
#Predicted Rate of Change
We could have an average dwell time of 1 day by 2027.
If you summarize the rate of change over the prior 12 years of Mandiant’s data, the average is a 25% reduction year over year, with a 37% decrease (read: sped up by 37%!) last year. Extrapolating that rate into the future, 2024 (reported next year in 2025) may be the first year where Mandiant’s average dwell time will be under a week (<7 days). If you extrapolate it out further, by 2027, we could have an average dwell time of one day. 2027 is not that far away! While the overall dwell times will continue to be spread out across a distribution, they will clump lower and lower, until the fastest dwell times on the lower quartile are just minutes.
#What This Means for Defenders
The cost to continue the status quo by keeping a human in the loop for every detection & response scenario is skyrocketing. To do so with the dwell time trajectory we’re on will require more security professionals than ever before, in order to monitor, triage, and make containment decisions. Assuming this is still the approach we should take, even finding the personnel, after the entire cybersecurity industry has bemoaned for years about a lack of millions of qualified people for existing unfilled roles, will be daunting.
Or we must acknowledge that another entirely different approach is needed.
Realistically, the cost to keep a human in the loop at this pace is untenable and will be abandoned. The question is: which approach will you take as a defender?
Will you:
-
Outsource the responsibility to a trusted third-party MSSP and make this their problem to solve on your behalf? What if you work for one of those MSSPs, what will you do about it?
-
Hop on the AI bandwagon and ignore LLM hallucinations, untraceable black boxes, expensive compute, data privacy issues when sending your sensitive security data to a third party AI model, and AI vendors who don’t appear to honor their word? (Exhibit A: a certain AI company’s legal situation with a certain leading actress over use of her voice & likeness without authorization.) Also, none of these AI solutions claim they can actually completely eliminate humans from the alert triage process. What confidence do we have that AI will actually solve this problem?
Or:
- Come see what Wirespeed built: an approach that doesn’t require a human-in-the-loop, is completely traceable and transparent, doesn’t introduce new problems, but remains supervised by expert humans following a proven quality process that you can audit. (And cheaper, too.)
Want to see what option 3 is all about? Start your own FREE Trial online in minutes right now. Follow us on LinkedIn / X or join our mailing list.