

Josh Moore
Founding Security Engineer
A classic BEC
A real-time anatomy lesson of a Business Email Compromise
#Trails tell stories
As a kid growing up in rural Southern Arkansas, family hunting trips were a common pastime of mine. One of the many things my dad taught me was to always learn the lay of the land prior to the hunt and find signs of activity for a better chance of success.
No matter where you hunt, wildlife has a tendency to find the path of least resistance. Around the dense stuff. Along dry creek beds. It’s not magic, it’s just efficiency. Why navigate through thick brush and thorns when there’s an easier way?
Every deer, turkey, every coyote follows the same logic: when going somewhere, do it the easiest way possible.
Threat actors are no different.
#Why hack the planet when you can just forward an invoice?
Verizon’s 2025 Data Breach Investigations Report notes that 99% of threat actors targeting SMBs are financially motivated [1]. The FBI’s data from 2024 shows us where that materializes: while ransomware accounted for 12.4 million in losses over 3,156 complaints, it pales in comparison to the $2.7 billion in losses attributed to BEC across 21,442 complaints. For the math-wiz out there, that’s than a 217x difference! [2].
BEC is 217x higher than Ransomware
#Why the massive gap?
Ransomware requires playing the long game. It usually goes something like this: threat actors have to phish or exploit a vulnerability to get Initial Access (or buy the access from another threat actor who got the access but doesn’t want to complete the objective), evade EDR, establish persistence, move laterally, stage and deploy tools, potentially exfiltrate data for double-extorion, encrypt systems, and then after all that, try to negotiate a payout. High effort, high noise, and a lot of ways it can fall apart.
Alternatively, they can just…log in and ask for money.
Business Email Compromise is the modern threat actor’s trail; their path of least resistance. They steal credentials (or just sessions), monitor inboxes, impersonate their victims and ask their business partners to reroute payments to the threat actor’s bank, or sometimes just the victim’s access to modify payments directly. It’s lower friction, lower risk and often, a faster route to payout.
#BEC in action
Last week, we got a front-row seat to a Business Email Compromise (BEC) targeting a financial user at one of our client organizations.
The first indicator came from Microsoft: a login to one of the user’s accounts from an Akamai IP address (172.236.106.184) using the Microsoft Edge browser on Windows 10 at 04:22:27 pm UTC. This was an Adversary in the Middle (AiTM) phishing proxy which bypassed MFA and captured a login session of the victim. [Pay close attention to that OS and User-Agent.]
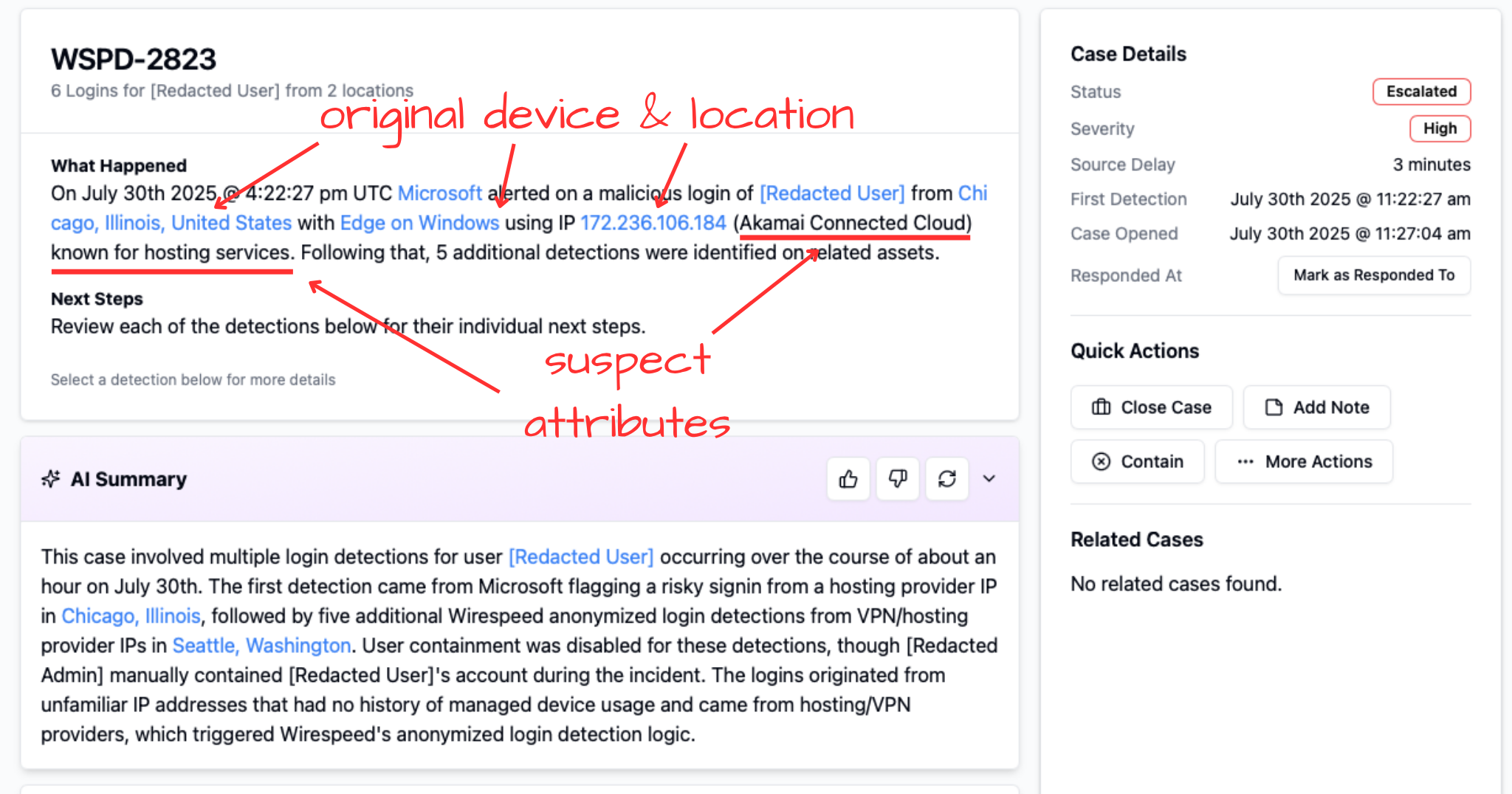
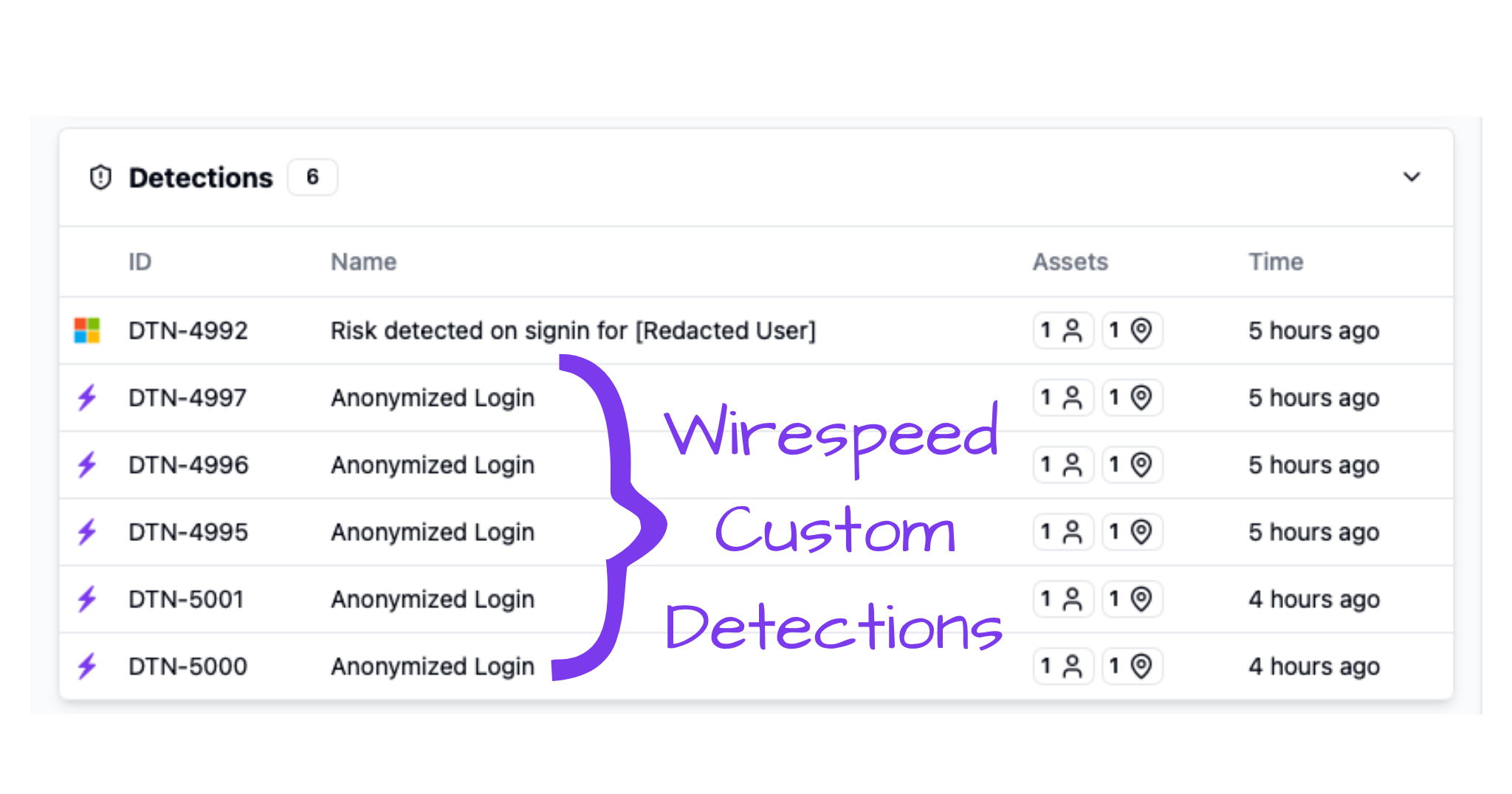
We recently rolled out our take on custom detections which not only detect, but triage immediately upon detection. In this case, our Anonymized Login detections identified five suspicious logins that Microsoft missed.
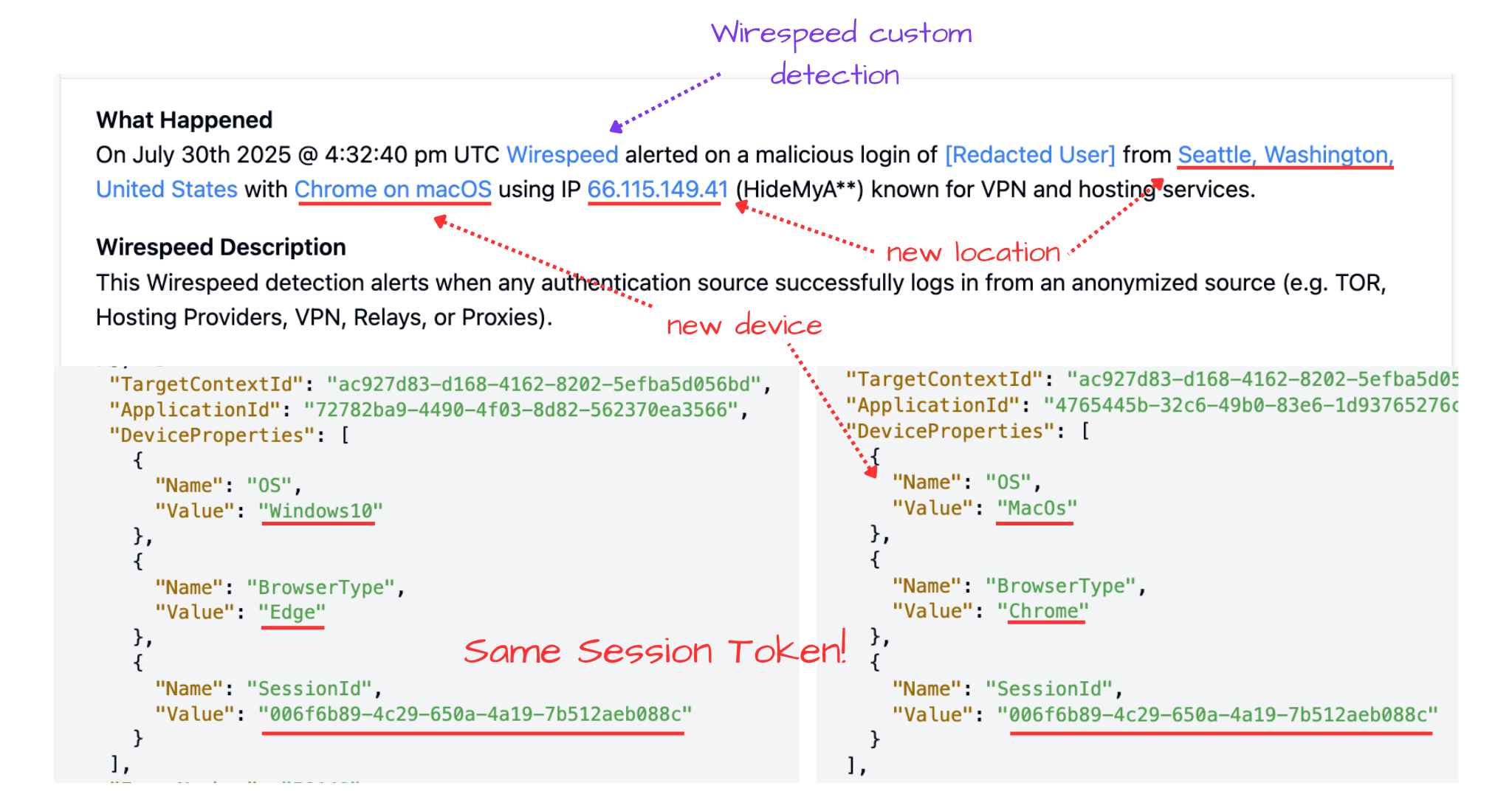
Diving into the first Anonymized login, we see at 04:32:40 pm UTC a login reused the same session token but this time the browser is Chrome on MacOS not Edge on Windows 10 like the first event. With a “bite” on their phish, the attacker switched to using the stolen access interactively from a privacy VPN.
We see ATO (account takeovers) all the time, but often without material impact, most likely because the attacker triaged the stolen account’s access and realized there was no access to monetize (i.e they’re not a technical user for ransomware, nor are they a financial user for BEC wire fraud). In this case, the attacker saw an angle. At 04:34:15 PM UTC the attacker, now using the VPN IP and wasting no time, added two mailbox rules to the accountant’s mailbox:
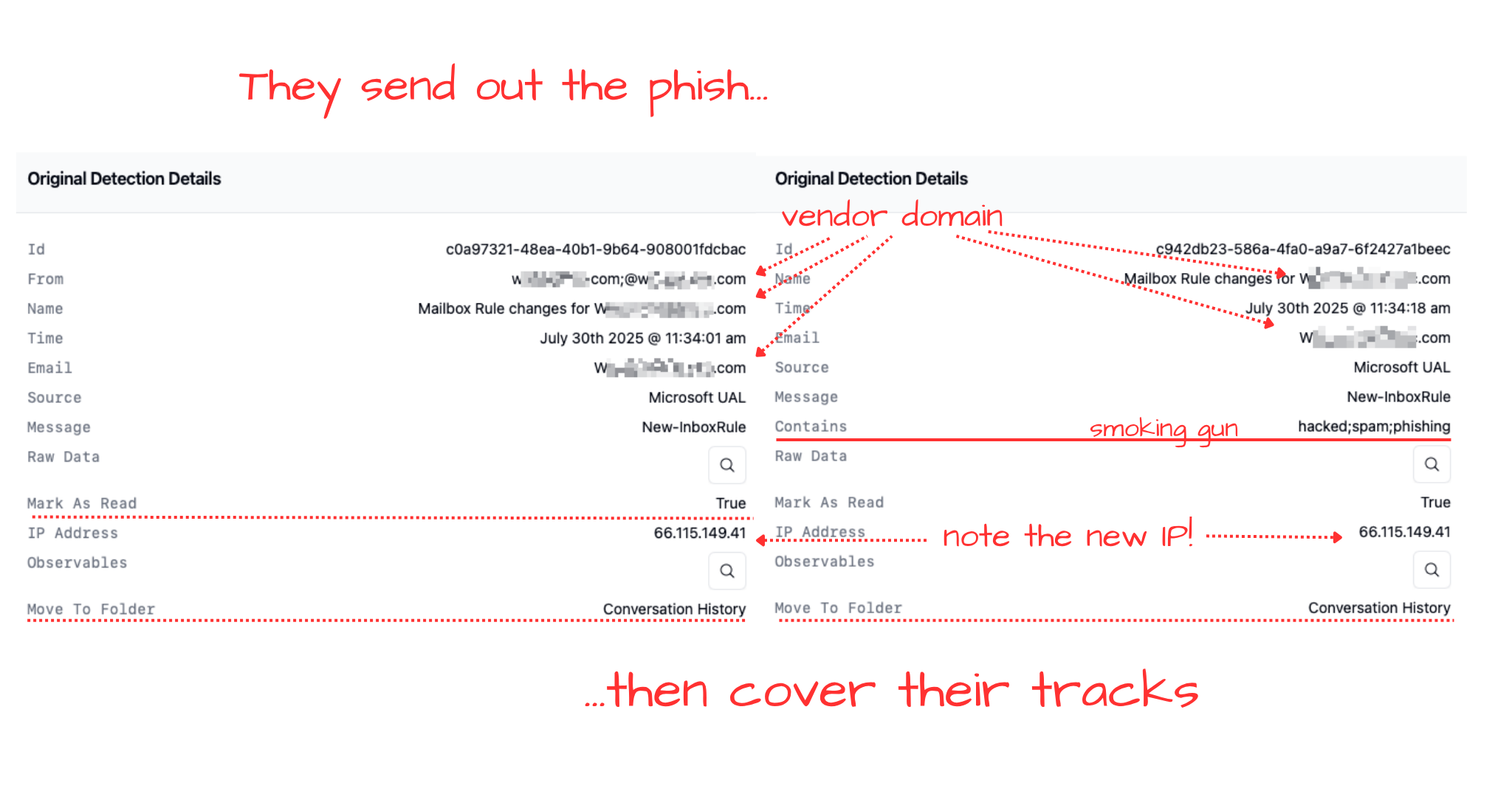
- Rule One: For emails from a targeted business partner, mark them as read and move them to the
Conversation Historyfolder, so the victim can’t see the conversation. - Rule Two: Do the same with any emails containing keywords: “hacked,” “spam,” or “phished” so any complaints don’t raise alarms.
We detected the initial ATO, the session reuse, the mailbox rule creations, all in real-time, but not every client is ready for automated response.
With great power, comes great responsibility.
– Uncle Ben
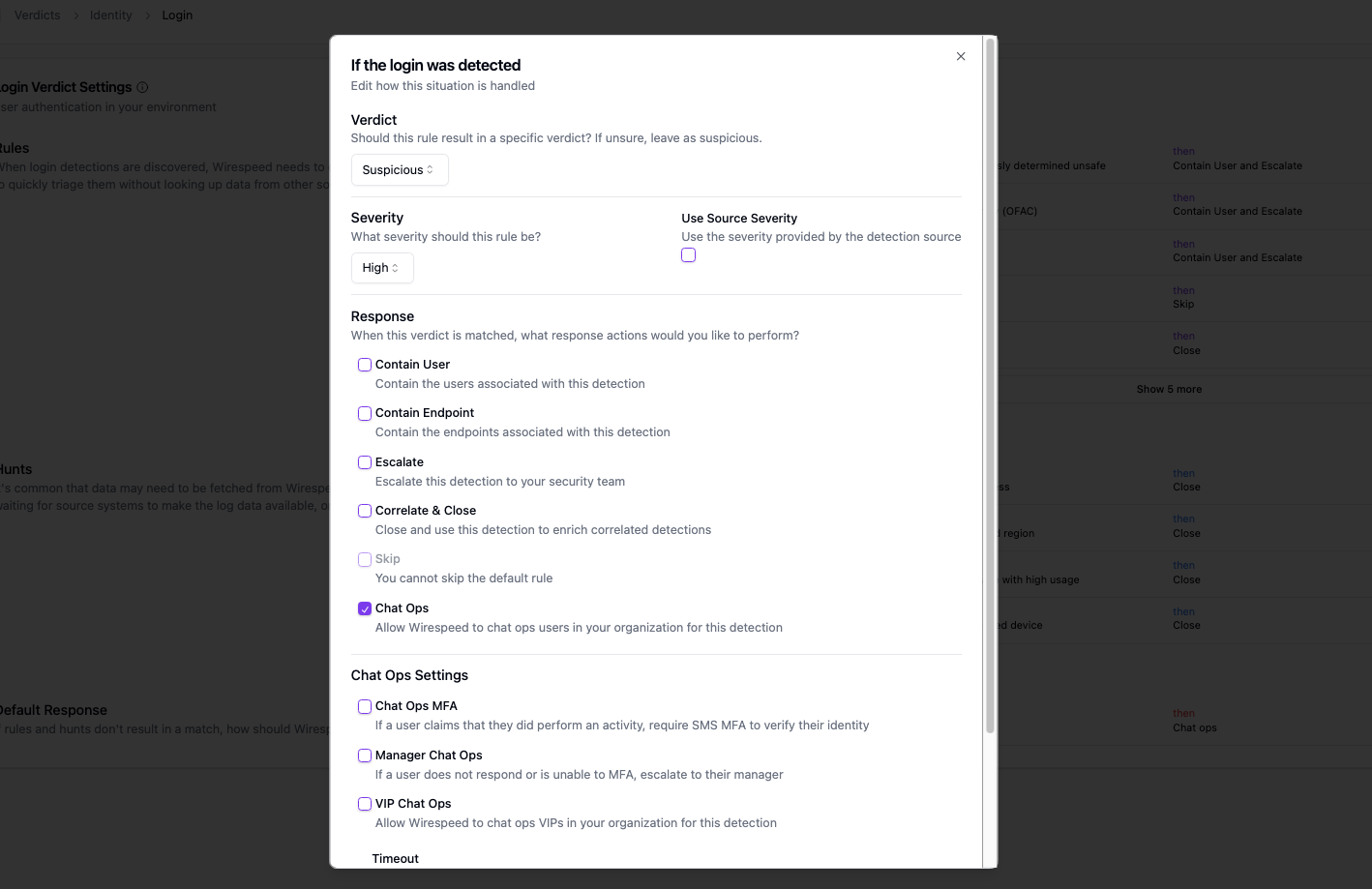
Our clients deserve choice since it’s their environment. Legacy MDR either forces a one-size-fits-all response or some ugly amalgamation of wiki pages and sticky notes to remember client requests (I’ve seen both first hand!). We let customers decide what should be blocked, escalated, or ignored.
This is how MDR always should’ve been.
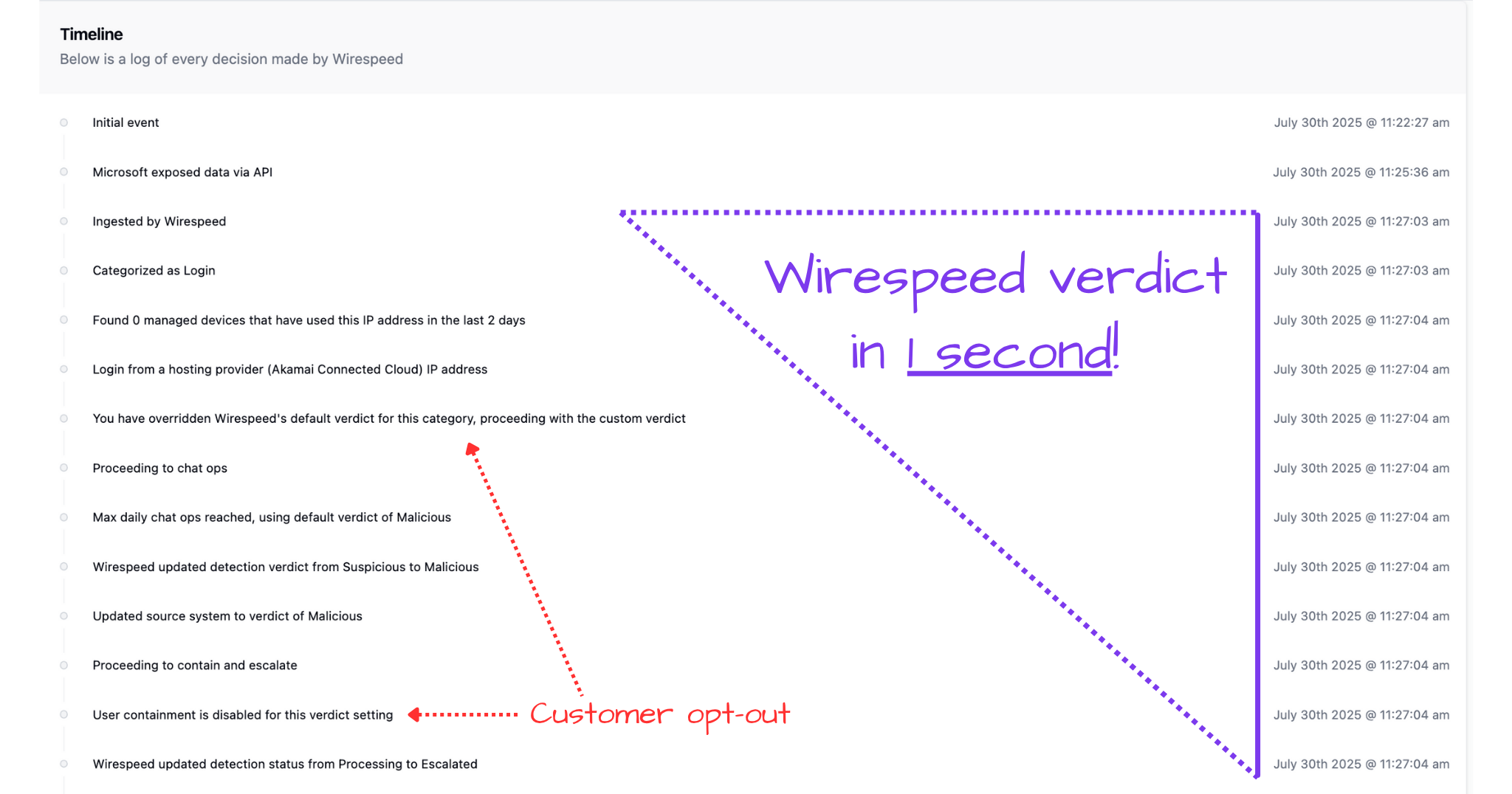
Our default settings would have contained in one second. Check out the timeline:
#The Path of Most Resistance
Ironically, we *haven’t* taken the path of least resistance. We’ve done the opposite: we’ve taken the path of most resistance. We can triage, verdict, and respond in seconds because we know every investigation process before it happens. Predefined, expertly-crafted, and consistently executed. Rather than go the easy route, we chose the alternative: all the hard work to clean up the thorns and brush to make a newer and easier trail for you. Try us out today.
#Sources

Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.