
Tim MalcomVetter
Co-Founder / CEO
This is part 2 of Identity Crisis.
The Tale of a Mechanical Engineer’s Loose Credentials
A couple months ago, we onboarded a small U.S. based enterprise, with virtually no business reasons to travel abroad, for an evaluation of Wirespeed MDR. They also thought their security was pretty good and that they knew everything going on. What happened next was quite astounding…
As part of our onboarding process, every time we add an integration, we pull all telemetry from the previous 90 days and immediately triage it. For a company their size, all of the cases were completely triaged by the time they hit “Enter” and then navigated to the case view in our UI. Living up to our Wirespeed name, it only took a few seconds.
One thing immediately stood out: a mechanical engineer, whose work keeps him planted domestically within the U.S., was promiscuously logging in from all over the globe—and not with privacy VPNs, because with our IPInfo partnership, we can tell the difference.
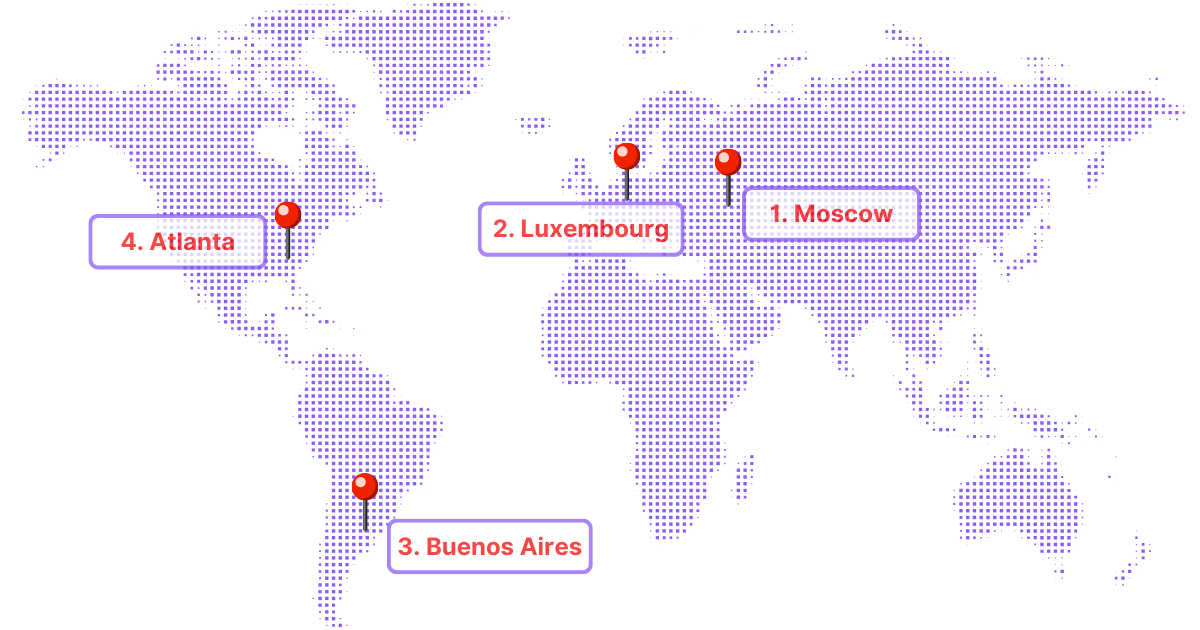
This engineer’s most recent 24 hours looked like the map above:
- First, a login from Moscow, Russia
- A couple hours later, a login from Luxembourg
- About 6 hours after that, a login from Buenos Aires, Argentina
- Finally, 2 hours later, a legitimate login from the Atlanta metro area during normal business hours
Whew! There wasn’t even time for jet lag! He had to be flying supersonic! To make it worse, this had been going on every single week for the last 3 months—logins from everywhere!
#Where was the Material Impact?
Short answer: there wasn’t any material impact…
At least not yet.
Q: But why?
A: Because the victim in this case, the mechanical engineer, was missing two primary ingredients for the common thieves breaking into this client’s infrastructure:
#1. He had no Technical Access.
He was a mechanical engineer, not a software engineer or an IT admin. His day job involved fabrication of physical objects the company sold. He didn’t administer M365 or show any clear path to Domain Admin, their clould infrastructure, or any other king of the hill. So, there was no (easy?) way to turn his access into Ransomware.
#2. He had no Financial Access.
He didn’t send invoices to clients. He didn’t have access to the company’s general ledger, the ERP system, the company bank accounts, employee payroll ACH settings, or any other avenues to commit financial fraud. So he wasn’t a good victim for BEC (Business Email Compromise), where bad guys trick business partners or other related parties into sending their funds to the wrong place—an account the attacker controls, ready for immediate liquidation out of the country.
#So the crooks moved on
Week after week, sometimes more than once in a day, a bad guy logged into the mechanical engineer’s account from a different corner of the world. Each subsequent login didn’t look like the same bad guy. There was no real overlap in infrastructure or behaviors, other than they didn’t stay interested for long, and the company never experienced any material losses.
The only sensible way to explain this behavior: the attackers triaged their access from his credentials, didn’t see a quick path worth investing their time to monetize his access the common ways they know how.
But how did so many different attackers continually get into the mechanical engineer’s account?
#When in Doubt, Check the InfoStealer Logs
The most likely answer for scenarios like this, today, is an InfoStealer infection. InfoStealers are malware that simply collect passwords, session cookies, and other credentials from an infected device, and upload them to a shared location, most commonly encrypted Telegram channels. Since Telegram is open for anyone to access, this is a way for a malware developer to disassociate their access from the infected computer, but in exchange for anyone being able to access the stolen credential data. InfoStealers are especially prolific on personal/consumer devices, where security controls are more relaxed (i.e. no EDR), and the victims are more likely to get infected by shady drive-by downloads.
Sure enough, we checked our favorite InfoStealer logs and this mechanical engineer’s credentials were floating around for at least 3 years on Telegram.
The InfoStealer logs showed:
- The infected computer was running Windows 10 Home Edition
- There wasn’t any EDR, but there was freeware anti-virus installed (which is easier to bypass)
- The malware was running from
C:\Users\john-doe\Downloads\COD4-modern-warfare-cracked-warez.exe - The victim’s plaintext password was barely capable of passing default Microsoft complexity rules
#Takeaways …
Obviously, there are many things we can learn from this.
#1. Lacking Policies
The company didn’t enforce a good password aging policy (his password hadn’t been rotated since before Azure Active Directory was a product).
#2. Missing MFA
The company didn’t enforce MFA on the mechanical engineer’s account. Maybe he was a long time employee, a really nice guy, important enough to keep happy, and he complained about the “hassle” of MFA, so they let him have an exception? Just guessing, since scenarios like that happen all the time, especially in smaller organizations.
#3. Unmanaged Devices
This was clearly a home PC, so they should look into enforcing managed devices only through MDM instead of letting unmanaged devices with who knows what running on them.
#4. Pirated Software
Users need to be educated about the dangers of downloading pirated software, which is commonly “given away” in exchange for the recipient to run shady gray-ware or malware embedded within the pirated version. Since this was a video game, we can give the benefit of the doubt it was a teenage kid in the house and this was a shared home computer, maybe, but it only reinforces number three above.
#5. Password Reuse
Password reuse is still a concern, because we saw variants of this password in more than one related InfoStealer log, associated with the victim’s identity across multiple websites and domains.
#The Best Part
We simply forced a password reset, enabled MFA, and our John Doe hasn’t had a single suspicious login in months since!
Continue with Part 3 of Identity Crisis.
Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.