
Tim MalcomVetter
Co-Founder / CEO
“Lateral Movement in 47 Seconds”
We have said from the beginning that adversaries are speeding up, but we recently clocked an adversary attempting lateral movement in a blazing 47 seconds! 🔥
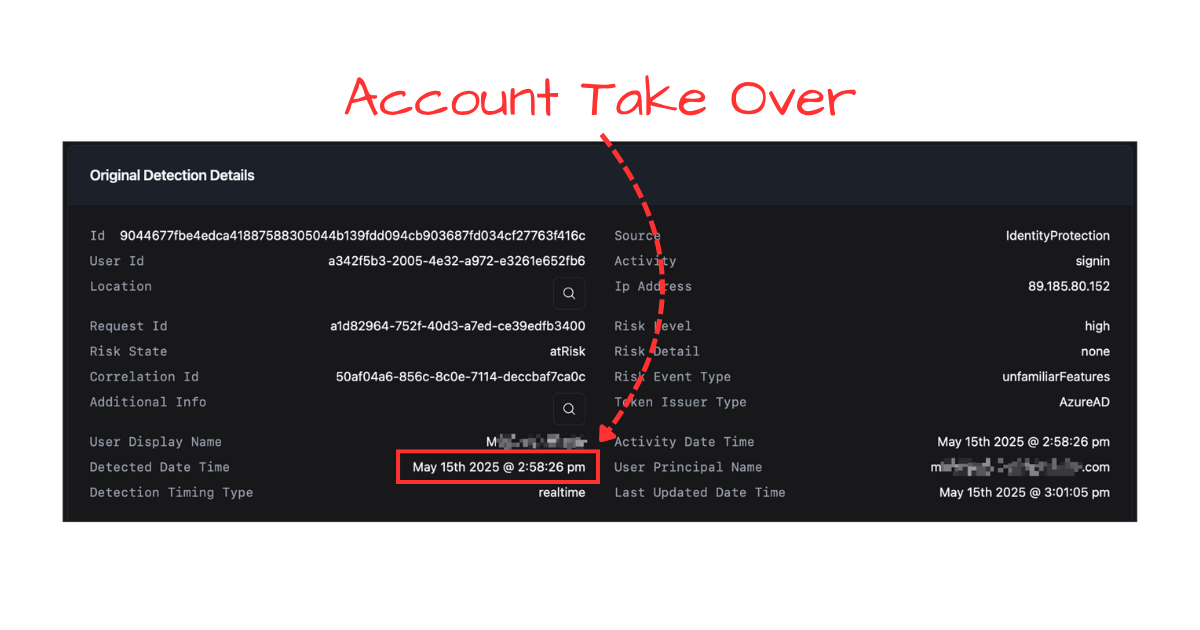
#Step 1: Account Take Over (ATO)
The first victim was compromised via an AiTM (adversary in the middle) phish, which can take over an account even with MFA. In scenarios like this, it’s common for the first ATO login event to happen from behind a hosting provider, just like this example. We are seeing these so often, we are almost to the point where we don’t care how the user authenticated, if they had MFA or not (unless it’s FIDO2 passkeys), because MFA is not stopping attackers these days, especially for BEC (Business Email Compromise).
#Step 2: Internal Lateral Movement Phish
A whopping 47 seconds later, from a totally different IP address belonging to T-Mobile in New York City, the attacker sent a phish from the first victim’s email account to her internal colleague. Because these go internal-to-internal, phishing protections are limited if effective at all. This also abuses trust relationships that are present between two colleagues, making the phish lure more believeable. (This is a tactic I have personally successfully employed in Red Team engagements years ago).
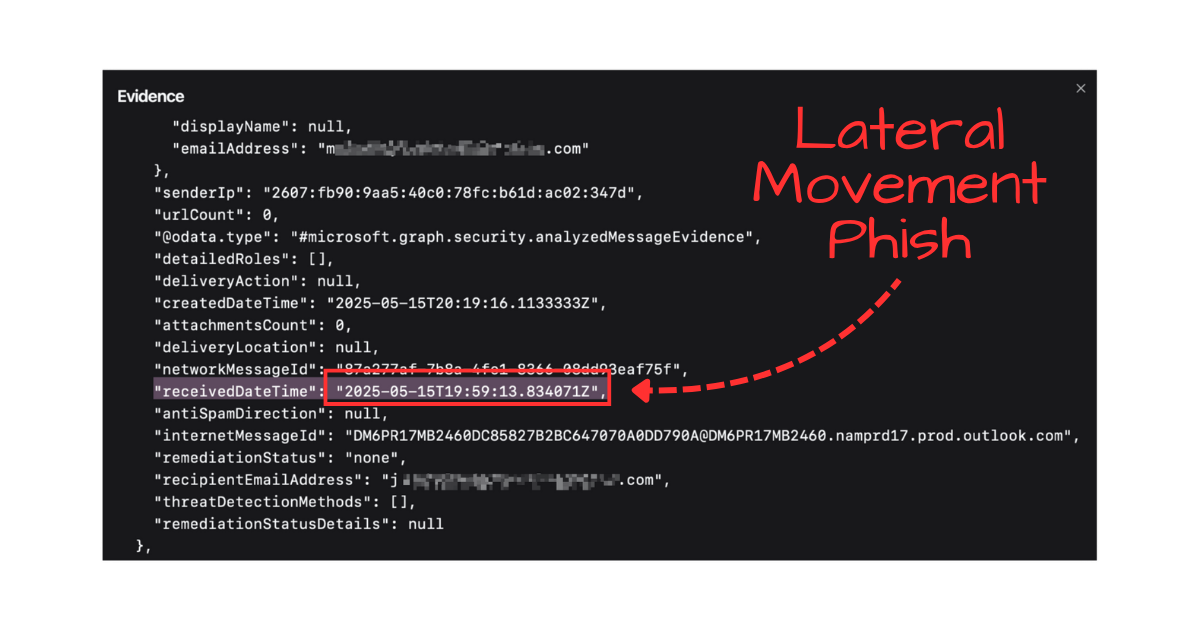
Finding a colleague to become the second victim and actually send them the email in 47 seconds means the attacker was highly automated. A script likely took the session token from the first AiTM phish, made an API call to the victim’s mailbox, discovered a colleague out of recent email conversations as the next target, and then sent the second email phish.
Fortunately for us, we contained the victim user’s account and the phishes weren’t clicked by the second victim, so our customer had zero material impact from this temporary incursion.
#20 Minute MTTR (Mean Time To Respond)
For the past few years, one of the big MDR companies advertised their 23 minute MTTR times. Any approach that results in MTTR times in the 10+ minutes range is woefully unprepared for the realities of where attackers are headed. Imagine how many additional victims could have received phishes, clicked them, and they themselves also started sending phishes to more colleagues, in 23 minutes. It’s terrifying to consider trying to keep up with attackers using a legacy, human-triage approach.
Fortunately for our customers, we triaged this case in under 1 second, and immediately intiated containment and escalation procedures. The biggest bottleneck is the ingestion delay upstream from us, in this case from Microsoft.
Be faster!
Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.