

Tim MalcomVetter
Co-Founder / CEO
Microsoft Identity Challenges
Most internal/enterprise SOC teams struggle to triage every single suspicious login detection. Outsourced SOC teams struggle even more, because if corporate security teams don’t know where their people are (and most legal teams are allergic to invading their employees’ privacy), how can your outsourced security provider?
This is an example from a Wirespeed customer just yesterday:
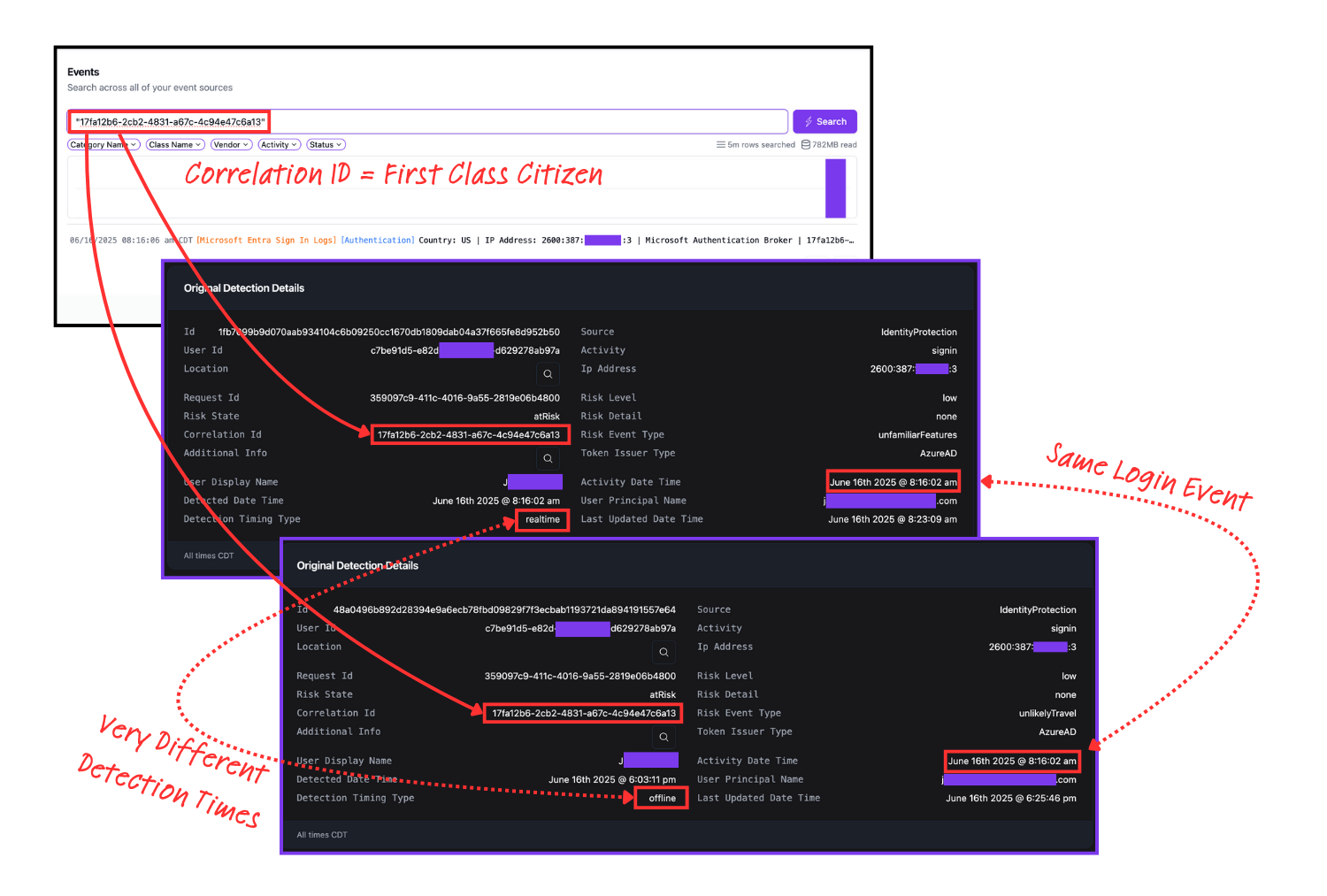
Let’s list out the investigation challenges here:
- John Doe logs in at 8:16:02 AM
- Microsoft fires a “realtime” detection, flagging something unfamiliar about the login
- If you don’t pay the “Security Tax” (E3/E5 licensing) good luck figuring out what Microsoft thought was “unusual”
- Also note: “realtime” to Microsoft is 9 minutes later (8:23:09 AM)!
- TEN HOURS LATER … Microsoft generates an “offline” detection of unlikely travel!
- The actual login event was 8:16:06 AM, not 8:16:02 AM (four seconds earlier - at scale, little differences like this are huge)
#How these confusing details derail investigations
At full-speed and full-scale, there are so many ways these end up wasting precious security personnel hours:
- By working them separately, thinking they are two distinct events given the 10 hour delta in alerting
- By not being able to locate the actual login event with metadata that is missing from the alerts
- By not being able to determine what is “unusual” about the login without the highest of Microsoft licensing
But the worst problem is:
- Security teams grow numb to identity alerts, because so many are false positives, that they miss when a real attacker logs in.
That is what concerns us at Wirespeed, where we typically see at least 3 times as many identity detections for every endpoint detection. With EDR deployments everywhere, attackers find more success with identities.
#How Wirespeed makes this better
As you can see from all three of the above screenshots, there is a single GUID present across all of them, called the CorrelationId. This is like a meta/session ID that links all of the activity together. In our world, this value is a first class citizen, which means you can simply paste it into the Events Search in our data lake powered by Clickhouse and you instantly get back the fully-hydrated Open Cybersecurity Schema Framework (OCSF) event, making it very clear these are, in fact, all one and the same event.
This is just one of many ways we handle Identity Detections.
Want to learn more about how Wirespeed can make security painless for you? Contact us to start a FREE TRIAL today.