

Tim MalcomVetter
Co-Founder / CEO
How we handle Attack Simulations
What’s the best way for a SOC to handle alerts from a simulated attack?
- Miss the presence of the BAS (breach and attack simulation) tools entirely
- See the BAS tools, confidently dismissing it as “obvious testing activity”
- Spot the BAS tools, wrap up all the activity in a single case, treat it as real (because you never know with bad guys)
We do option 3.
This is a situation where security practitioners of all walks of life will each have their own opinion. In past roles, I have been yelled at for both: A) NOT telling a customer about pentest or red team activity when our SOC assumed it was a test, and B) telling a customer about observed obvious testing activity because “it’s obviously a test, so don’t bother me.”
Sometimes you can’t win. 🤷
My bias, since my days doing red team work, has always been to err on the side of caution and escalate behavior that may be testing activity. Why? For one, because we have a whole historical pattern of real bad guys copying red teamers, who think they’re copying real bad guys. It goes on and on in a circle, and the nation state APT groups hopped onto that merry-go-round as well. What better thing for a nation state actor than to be mistaken for a common “good guy” red teamer?
The fancy cyber word for that is “cohabitation.” If there is a possibility of a real threat actor cohabitating with a known tester, it creates a massive deconfliction problem during incident response. So, in our red team rules of engagement we stood down until deconfliction was complete—and that stuck with me!
On the flip side, though, we can’t just ignore the indicators of likely attack simulation tools and play dumb, because you end up looking … well … dumb. So we chose a middle ground path for Wirespeed:
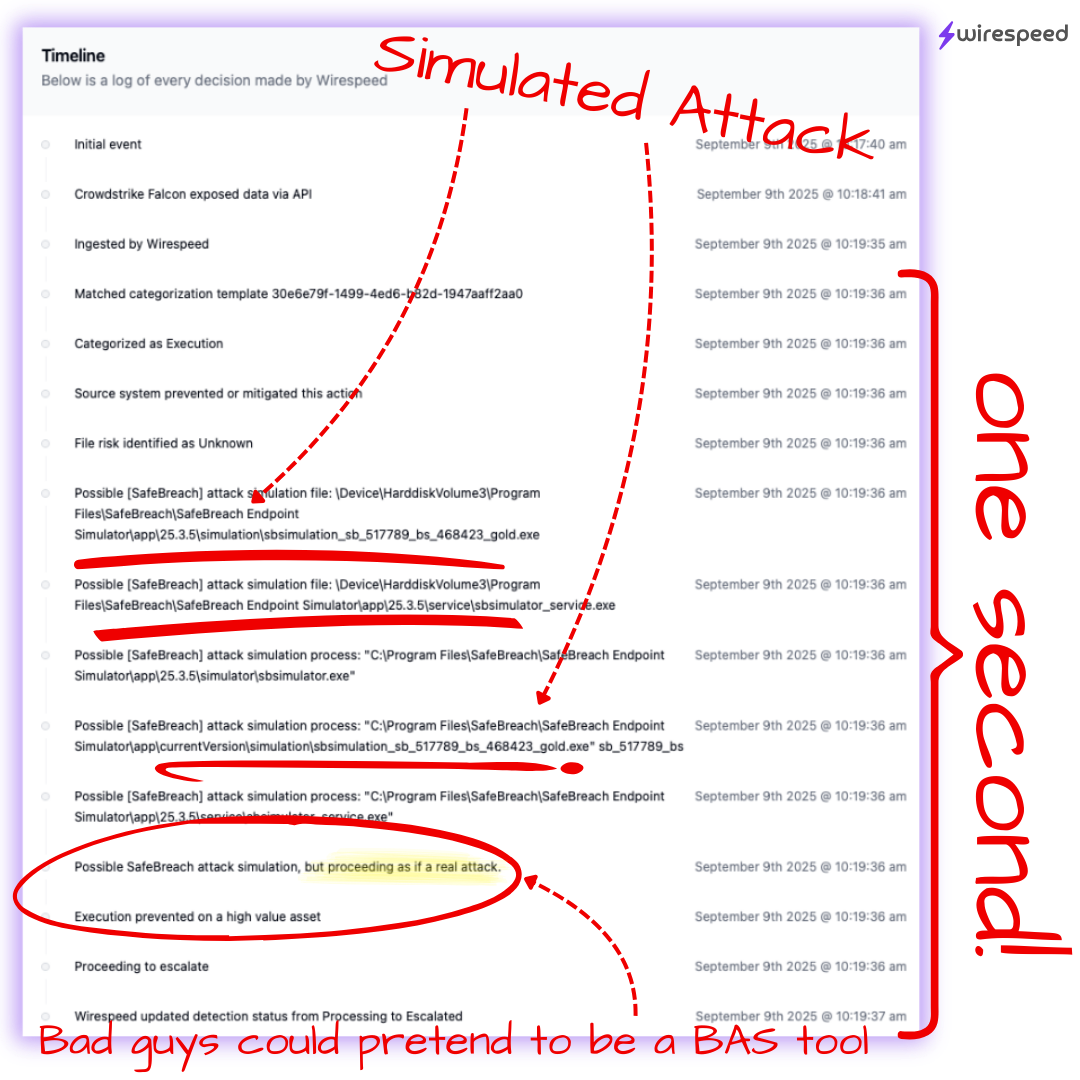
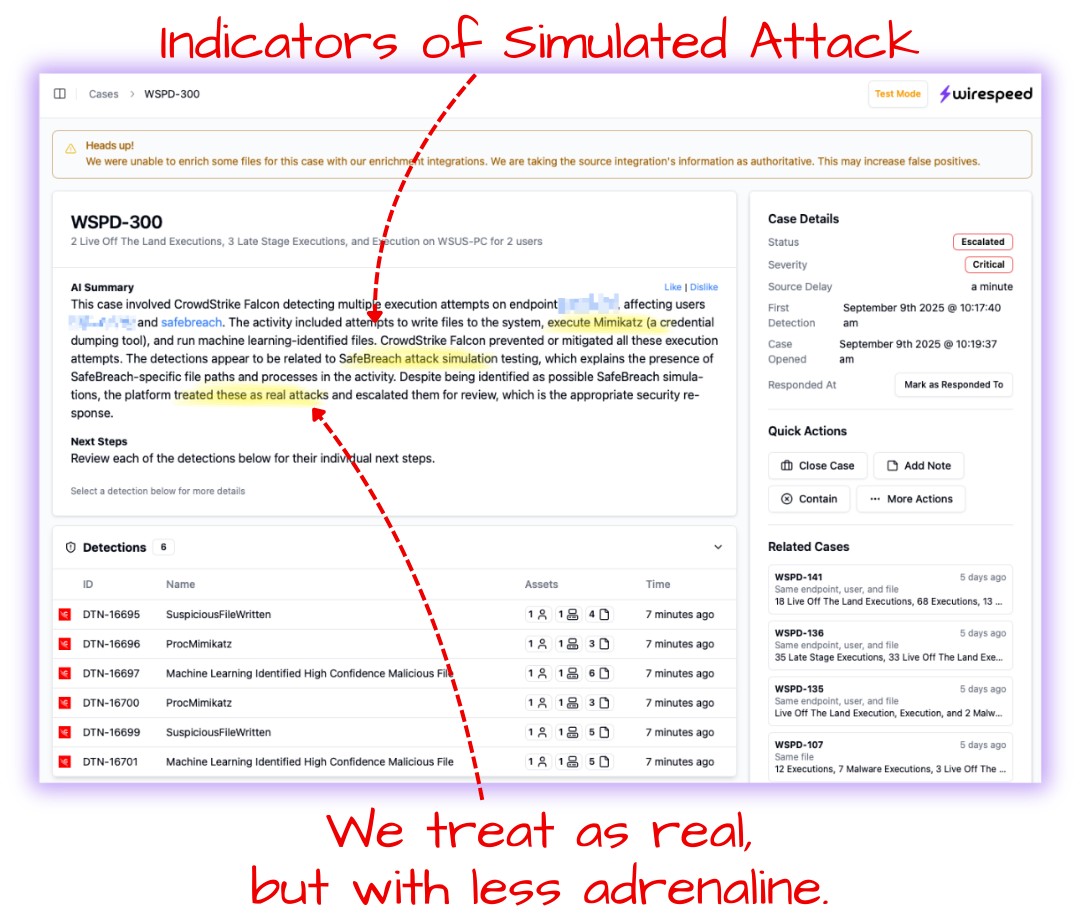
We check for the presence of most BAS tools based on signatures we have about them. Is it perfect? No way! But does it pop helpful signals like this on cases? Absolutely.
But … can it be wrong and mask a real attacker? Sure. Although, real attackers tend to do more lateral spread and be a little less noisy (usually). But the fact that it could be a real actor is why we still continue our verdict process, escalating or containing endpoints and users for you.
In the screenshot above, where the customer was evaluating Wirespeed by launching Safe Breach on an endpoint, we only escalated (due to test mode), but we would have absolutely contained it under production-ready conditions, because guess what: you need to know that all of the steps and pieces work together!
#A little less adrenaline …
The biggest benefit to our middle ground approach is that it definitely gives our customers a little less adrenaline and heartburn when we calmly tell them we see the presence of the attack sim tool, but worked the case anyway.

Want to see how your attack sim tool would look with Wirespeed? Contact us to start a FREE TRIAL today.